Security News
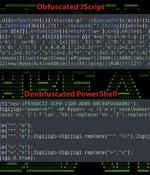
Cybersecurity researchers have discovered an ongoing phishing campaign that makes use of a unique attack chain to deliver the XWorm malware on targeted systems. Securonix, which is tracking the activity cluster under the name MEME#4CHAN, said some of the attacks have primarily targeted manufacturing firms and healthcare clinics located in Germany.

A nascent botnet called Andoryu has been found to exploit a now-patched critical security flaw in the Ruckus Wireless Admin panel to break into vulnerable devices. While the malware is known to weaponize remote code execution flaws in GitLab and Lilin DVR for propagation, the addition of CVE-2023-25717 shows that Andoryu is actively expanding its exploit arsenal to ensnare more devices into the botnet.

Cybersecurity researchers have shed light on a new ransomware strain called CACTUS that has been found to leverage known flaws in VPN appliances to obtain initial access to targeted networks. "Once inside the network, CACTUS actors attempt to enumerate local and network user accounts in addition to reachable endpoints before creating new user accounts and leveraging custom scripts to automate the deployment and detonation of the ransomware encryptor via scheduled tasks," Kroll said in a report shared with The Hacker News.

A new proof-of-concept exploit for an actively exploited PaperCut vulnerability was released that bypasses all known detection rules. The PaperCut vulnerability, tracked as CVE-2023-27350, is a critical severity unauthenticated remote code execution flaw in PaperCut MF or NG versions 8.0 or later that has been exploited in ransomware attacks.
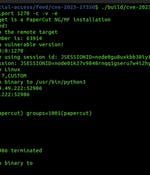
Cybersecurity researchers have found a way to exploit a recently disclosed critical flaw in PaperCut servers in a manner that bypasses all current detections. Tracked as CVE-2023-27350, the issue affects PaperCut MF and NG installations that could be exploited by an unauthenticated attacker to execute arbitrary code with SYSTEM privileges.

CVE-2018-9995 is an authentication bypass vulnerability that can be triggered with a simple exploit sent via a maliciously crafted HTTP cookie to a vulnerable DVR device. The device responds by sending back the device's admin credentials in clear text.

Infoblox Threat Intelligence Group, which says it analyzes billions of DNS records and millions of domain-related records each day, has reported a new malware toolkit called Decoy Dog that uses a remote access trojan called Pupy. InfoBlox found that the Decoy Dog toolkit that uses Pupy in fewer than 3% of all networks, and that the threat actor who has control of Decoy Dog is connected to just 18 domains.

Hackers are actively exploiting an unpatched 2018 authentication bypass vulnerability in exposed TBK DVR devices. Fortinet's FortiGard Labs reports seeing an uptick in hacking attempts on TBK DVR devices recently, with the threat actors using a publicly available proof of concept exploit to target a vulnerability in the servers.

VMware has released security updates to address zero-day vulnerabilities that could be chained to gain code execution systems running unpatched versions of the company's Workstation and Fusion software hypervisors. The two flaws were part of an exploit chain demoed by the STAR Labs team's security researchers one month ago, during the second day of the Pwn2Own Vancouver 2023 hacking contest.

An unauthenticated RCE flaw in widely-used PaperCut MF and NG print management software is being exploited by attackers to take over vulnerable application servers, and now there's a public PoC exploit. According to PaperCut, the attacks seem to have started on April 14, 2023 - a month and a week after the software maker released new PaperCut MF and NG versions that fixed CVE-2023-27350 and CVE-2023-27351, an unauthenticated information disclosure flaw that could allow attackers to access sensitive user information without authentication.