Security News

Citizen Lab says two zero-days fixed by Apple today in emergency security updates were actively abused as part of a zero-click exploit chain to deploy NSO Group's Pegasus commercial spyware onto fully patched iPhones. The two bugs, tracked as CVE-2023-41064 and CVE-2023-41061, allowed the attackers to infect a fully-patched iPhone running iOS 16.6 and belonging to a Washington DC-based civil society organization via PassKit attachments containing malicious images.

Mozilla on Tuesday released security updates to resolve a critical zero-day vulnerability in Firefox and Thunderbird that has been actively exploited in the wild, a day after Google released a fix for the issue in its Chrome browser. The shortcoming, assigned the identifier CVE-2023-4863, is a heap buffer overflow flaw in the WebP image format that could result in arbitrary code execution when processing a specially crafted image.

Apple devices are again under attack, with a zero-click, zero-day vulnerability used to deliver Pegasus spyware to iPhones discovered in the wild. Researchers at Citizen Lab are referring to the exploit as BLASTPASS. The team said they immediately disclosed their findings to Apple when they first discovered an infected device owned by an individual employed by a Washington DC-based civil society organization with international offices.

North Korean threat actors are once again attempting to compromise security researchers' machines by employing a zero-day exploit. The warning comes from Google's own security researchers Clement Lecigne and Maddie Stone, who detailed the latest campaign mounted by government-backed attackers.

Threat actors associated with North Korea are continuing to target the cybersecurity community using a zero-day bug in unspecified software over the past several weeks to infiltrate their machines. A search on X shows that the now-suspended account has been active since at least October 2022, with the actor releasing proof-of-concept exploit code for high-severity privilege escalation flaws in the Windows Kernel such as CVE-2021-34514 and CVE-2022-21881.

The U.S. Cybersecurity and Infrastructure Security Agency on Thursday warned that multiple nation-state actors are exploiting security flaws in Fortinet FortiOS SSL-VPN and Zoho ManageEngine ServiceDesk Plus to gain unauthorized access and establish persistence on compromised systems. "Nation-state advanced persistent threat actors exploited CVE-2022-47966 to gain unauthorized access to a public-facing application, establish persistence, and move laterally through the network," according to a joint alert published by the agency, alongside Federal Bureau of Investigation, and Cyber National Mission Force.

Citizen Lab says two zero-days fixed by Apple today in emergency security updates were actively abused as part of a zero-click exploit chain to deploy NSO Group's Pegasus commercial spyware onto fully patched iPhones. The two bugs, tracked as CVE-2023-41064 and CVE-2023-41061, allowed the attackers to infect a fully-patched iPhone running iOS 16.6 and belonging to a Washington DC-based civil society organization via PassKit attachments containing malicious images.

Hackers are exploiting two recent MinIO vulnerabilities to breach object storage systems and access private information, execute arbitrary code, and potentially take over servers. MinIO is an open-source object storage service offering compatibility with Amazon S3 and the ability to store unstructured data, logs, backups, and container images of up to 50TB in size.
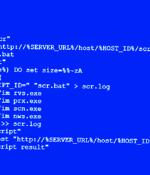
An unknown threat actor has been observed weaponizing high-severity security flaws in the MinIO high-performance object storage system to achieve unauthorized code execution on affected servers. Cybersecurity and incident response firm Security Joes said the intrusion leveraged a publicly available exploit chain to backdoor the MinIO instance.
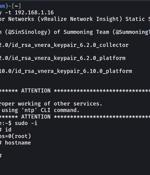
Proof-of-concept exploit code has been made available for a recently disclosed and patched critical flaw impacting VMware Aria Operations for Networks. "A malicious actor with network access to Aria Operations for Networks could bypass SSH authentication to gain access to the Aria Operations for Networks CLI," VMware said earlier this week.