Security News

Citizen Lab says two zero-days fixed by Apple today in emergency security updates were actively abused as part of a zero-click exploit chain to deploy NSO Group's Pegasus commercial spyware onto fully patched iPhones. The two bugs, tracked as CVE-2023-41064 and CVE-2023-41061, allowed the attackers to infect a fully-patched iPhone running iOS 16.6 and belonging to a Washington DC-based civil society organization via PassKit attachments containing malicious images.

Hackers are exploiting two recent MinIO vulnerabilities to breach object storage systems and access private information, execute arbitrary code, and potentially take over servers. MinIO is an open-source object storage service offering compatibility with Amazon S3 and the ability to store unstructured data, logs, backups, and container images of up to 50TB in size.
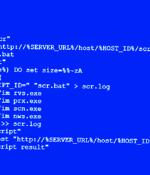
An unknown threat actor has been observed weaponizing high-severity security flaws in the MinIO high-performance object storage system to achieve unauthorized code execution on affected servers. Cybersecurity and incident response firm Security Joes said the intrusion leveraged a publicly available exploit chain to backdoor the MinIO instance.
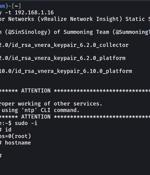
Proof-of-concept exploit code has been made available for a recently disclosed and patched critical flaw impacting VMware Aria Operations for Networks. "A malicious actor with network access to Aria Operations for Networks could bypass SSH authentication to gain access to the Aria Operations for Networks CLI," VMware said earlier this week.

Proof-of-concept exploit code has been released for a critical SSH authentication bypass vulnerability in VMware's Aria Operations for Networks analysis tool.Today, VMware confirmed that CVE-2023-34039 exploit code has been published online, two days after disclosing the critical security bug.

New findings show that malicious actors could leverage a sneaky malware detection evasion technique and bypass endpoint security solutions by manipulating the Windows Container Isolation Framework. Microsoft's container architecture uses what's called a dynamically generated image to separate the file system from each container to the host and at the same time avoid duplication of system files.

Recently disclosed security flaws impacting Juniper firewalls, Openfire, and Apache RocketMQ servers have come under active exploitation in the wild, according to multiple reports. "This flaw allows an unauthorized user to exploit the unauthenticated Openfire Setup Environment within an established Openfire configuration," cloud security firm Aqua said.

A new version of the DreamBus botnet malware exploits a critical-severity remote code execution vulnerability in RocketMQ servers to infect devices. The recent DreamBus attacks leveraging that flaw were spotted by researchers at the Juniper Threat Labs, who reported a spike in the activity in mid-June 2023.

According to the report, attackers favor Microsoft because of the potential to move laterally through an organization's Microsoft environments. If 4.31% seems like a small figure, Abnormal Security CISO Mike Britton pointed out that it is still four times the impersonation volume of the second most-spoofed brand, PayPal, which was impersonated in 1.05% of the attacks Abnormal tracked.
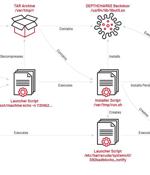
A suspected Chinese-nexus hacking group exploited a recently disclosed zero-day flaw in Barracuda Networks Email Security Gateway appliances to breach government, military, defense and aerospace, high-tech industry, and telecom sectors as part of a global espionage campaign. What's more, FOXTROT shares overlaps with an open-source rootkit called Reptile, which has been extensively used by multiple Chinese hacking crews in recent months.