Security News

A proof-of-concept (PoC) exploit for a critical-severity remote code execution flaw in Progress WhatsUp Gold has been published, making it critical to install the latest security updates as soon...

Cybersecurity researchers have disclosed a set of flaws impacting Palo Alto Networks and SonicWall virtual private network (VPN) clients that could be potentially exploited to gain remote code...

The recently uncovered 'Bootkitty' UEFI bootkit, the first malware of its kind targeting Linux systems, exploits CVE-2023-40238, aka 'LogoFAIL,' to infect computers running on a vulnerable UEFI...
A popular open-source game engine called Godot Engine is being misused as part of a new GodLoader malware campaign, infecting over 17,000 systems since at least June 2024. "Cybercriminals have...

Threat actors are using public exploits for a critical authentication bypass flaw in ProjectSend to upload webshells and gain remote access to servers. [...]
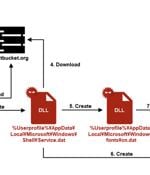
The threat actor known as APT-C-60 has been linked to a cyber attack targeting an unnamed organization in Japan that used a job application-themed lure to deliver the SpyGlace backdoor. That's...

A threat actor named Matrix has been linked to a widespread distributed denial-of-service (DoD) campaign that leverages vulnerabilities and misconfigurations in Internet of Things (IoT) devices to...

America's Cyber Defense Agency has received evidence of hackers actively exploiting a remote code execution vulnerability in SSL VPN products Array Networks AG and vxAG ArrayOS. [...]

The Russia-aligned threat actor known as RomCom has been linked to the zero-day exploitation of two security flaws, one in Mozilla Firefox and the other in Microsoft Windows, as part of attacks...

PAN-PAN! Intruders inject web shell backdoors, crypto-coin miners, more Thousands of Palo Alto Networks firewalls were compromised by attackers exploiting two recently patched security bugs. The...