Security News

The Danish energy sector has suffered what is believed to be the most extensive cyberattack in Danish history, according to SektorCERT. Danish energy sector under attack. From this vantage point, in May 2023, they detected three waves of attacks targeting companies in the energy sector.

In a rare display of transparency, US energy services firm BHI Energy details how the Akira ransomware operation breached their networks and stole the data during the attack. In a data breach notification sent by BHI Energy to impacted people, the company provides detailed information on how the Akira ransomware gang breached its network on May 30, 2023.

A Gaza-based threat actor has been linked to a series of cyber attacks aimed at Israeli private-sector energy, defense, and telecommunications organizations. Microsoft, which revealed details of...
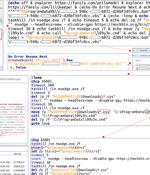
The Computer Emergency Response Team of Ukraine on Tuesday said it thwarted a cyber attack against an unnamed critical energy infrastructure facility in the country. "Visiting the link will download a ZIP archive containing three JPG images and a BAT file 'weblinks.cmd' to the victim's computer," CERT-UA said, attributing it to the Russian threat actor known as APT28.

Cofense, a U.S.-based email security company, released a new report about a massive QR code phishing campaign that targets numerous industries. QR codes are not often used in phishing campaigns; cybercriminals tend to use them more in day-to-day life, leaving QR codes in different places so curious people will scan them and possibly get scammed or infected by malware.

A phishing campaign was observed predominantly targeting a notable energy company in the US, employing QR codes to slip malicious emails into inboxes and bypass security. According to Cofense, who spotted this campaign, this is the first time that QR codes have been used at this scale, indicating that more phishing actors may be testing their effectiveness as an attack vector.

Microsoft is making it easier to see how much energy your apps use in Windows 11 over a given period by introducing a detailed power consumption page in the latest 23H2 update. The power consumption page provides a comprehensive report of energy use over the last 24 hours or the last seven days.

Security researchers are warning that tens of thousands of photovoltaic monitoring and diagnostic systems are reachable over the public web, making them potential targets for hackers. These systems are used for remote performance monitoring, troubleshooting, system optimization, and other functions to allow remote management of renewable energy production units.

The malware "Possesses the ability to steal information from various browsers, enabling the exfiltration of sensitive data, while also incorporating different modules for carrying out ransomware activities," Zscaler researchers Shatak Jain and Gurkirat Singh said in a recent analysis. Following a successful breach, the malicious binary is used as a conduit to set up persistence, perform the actual browser update, and also drop a stealer capable of covertly harvesting sensitive information and encrypting the stolen files, leaving the victims at risk of potential data loss, exposure, or even the sale of their valuable data.

Siemens Energy has confirmed that data was stolen during the recent Clop ransomware data-theft attacks using a zero-day vulnerability in the MOVEit Transfer platform.Today, Clop listed Siemens Energy on their data leak site, indicating that data was stolen during a breach on the company.