Security News

Three different threat actors leveraged hundreds of elaborate fictitious personas on Facebook and Instagram to target individuals located in South Asia as part of disparate attacks. "Each of these APTs relied heavily on social engineering to trick people into clicking on malicious links, downloading malware or sharing personal information across the internet," Guy Rosen, chief information security officer at Meta, said.

The cyber espionage actor tracked as Blind Eagle has been linked to a new multi-stage attack chain that leads to the deployment of the NjRAT remote access trojan on compromised systems. "The group is known for using a variety of sophisticated attack techniques, including custom malware, social engineering tactics, and spear-phishing attacks," ThreatMon said in a Tuesday report.

According to Mandiant, who has tracked APT43 since 2018, the threat actor aligns with the mission of the Reconnaissance General Bureau, the main foreign intelligence service from North Korea. In particular, malware and tools have been shared between APT43 and the infamous Lazarus threat actor.

As many as 55 zero-day vulnerabilities were exploited in the wild in 2022, with most of the flaws discovered in software from Microsoft, Google, and Apple. Of the 55 zero-day bugs, 13 are estimated to have been abused by cyber espionage groups, with four others exploited by financially motivated threat actors for ransomware-related operations.

The zero-day exploitation of a now-patched medium-security flaw in the Fortinet FortiOS operating system has been linked to a suspected Chinese hacking group. Threat intelligence firm Mandiant, which made the attribution, said the activity cluster is part of a broader campaign designed to deploy backdoors onto Fortinet and VMware solutions and maintain persistent access to victim environments.

ESET researchers have uncovered a compromise of an East Asian data loss prevention company. The attackers utilized at least three malware families during the intrusion, compromising both the internal update servers and third-party tools utilized by the company.
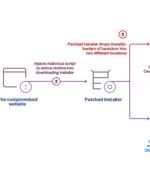
The cyber espionage threat actor tracked as Earth Kitsune has been observed deploying a new backdoor called WhiskerSpy as part of a social engineering campaign. The differentiating factor in the latest attacks is a shift to social engineering to trick users into visiting compromised websites related to North Korea, according to a new report from Trend Micro released last week.

In December 2022, security company Mandiant, now a Google Cloud company, identified a FortiOS malware written in C that exploited the CVE-2022-42475 FortiOS vulnerability. The Linux version of the malware, when executed, performs a system survey and enables communications with a hardcoded command-and-control server.

The threat actor targets high-profile and high-security accounts for cyberespionage purposes. Their favorite method to approach and attack their targets consists of using web beacons in emails before eventually attempting to harvest the target's credentials.

A threat actor with a suspected China nexus has been linked to a set of espionage attacks in the Philippines that primarily relies on USB devices as an initial infection vector. The reliance on infected USB drives to propagate the malware is unusual if not new.