Security News

Once they've broken into a victims' compute environment - often via compromised credentials - they keep quiet, deploying mining malware and then raking in cryptocurrencies using the stolen compute resources. Plus, according to security researchers, illicit mining is on the rise.

If you're running an Apache NiFi instance exposed on the internet and you have not secured access to it, the underlying host may already be covertly cryptomining on someone else's behalf. "Routers make bad cryptomining servers. Cryptomining may be what they end up doing if the lateral movement doesn't get them anywhere."

A financially motivated threat actor of Indonesian origin has been observed leveraging Amazon Web Services Elastic Compute Cloud instances to carry out illicit crypto mining operations. Cloud security company's Permiso P0 Labs, which first detected the group in November 2021, has assigned it the moniker GUI-vil.
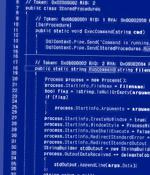
Poorly managed Microsoft SQL servers are the target of a new campaign that's designed to propagate a category of malware called CLR SqlShell that ultimately facilitates the deployment of cryptocurrency miners and ransomware. "Similar to web shell, which can be installed on web servers, SqlShell is a malware strain that supports various features after being installed on an MS SQL server, such as executing commands from threat actors and carrying out all sorts of malicious behavior," AhnLab Security Emergency response Center said in a report published last week.

Security researchers discovered a cryptomining operation targeting macOS with a malicious version of Final Cut Pro that remains largely undetected by antivirus engines. From the first generation, the malware used an i2p network layer for command and control communications to anonymize traffic.

A new malware dubbed 'ProxyShellMiner' exploits the Microsoft Exchange ProxyShell vulnerabilities to deploy cryptocurrency miners throughout a Windows domain to generate profit for the attackers. ProxyShell is the name of three Exchange vulnerabilities discovered and fixed by Microsoft in 2021.

A type of cryptomining malware targeting Linux-based systems has added capabilities by incorporating an open source remote access trojan called Chaos RAT with several advanced functions that bad guys can use to control remote operating systems. Like earlier, similar versions of the miner that also target Linux operating systems, the code kills competing malware and resources that affect cryptocurrency mining performance.

An automated and large-scale 'freejacking' campaign abuses free GitHub, Heroku, and Buddy services to mine cryptocurrency at the provider's expense. The operation relies on abusing the limited resources offered to free-tier cloud accounts to generate a tiny profit from each free account, which, when combined, becomes something more significant.

The malware was dubbed "Shikitega" for its extensive use of the popular Shikata Ga Nai polymorphic encoder, which allows the malware to "Mutate" its code to avoid detection. Shikitega alters its code each time it runs through one of several decoding loops that AT&T said each deliver multiple attacks, beginning with an ELF file that's just 370 bytes.

Watch out: someone is spreading cryptocurrency-mining malware disguised as legitimate-looking applications, such as Google Translate, on free software download sites and through Google searches. "The malware is dropped from applications that are popular, but don't have an actual desktop version, such as Google Translate, keeping the malware versions in demand and exclusive," Check Point malware analyst Moshe Marelus wrote in a report Monday.