Security News

A threat actor, presumably from Tunisia, has been linked to a new campaign targeting exposed Jupyter Notebooks in a two-fold attempt to illicitly mine cryptocurrency and breach cloud environments....
A legitimate Windows tool used for creating software packages called Advanced Installer is being abused by threat actors to drop cryptocurrency-mining malware on infected machines since at least November 2021. "The attacker uses Advanced Installer to package other legitimate software installers, such as Adobe Illustrator, Autodesk 3ds Max, and SketchUp Pro, with malicious scripts and uses Advanced Installer's Custom Actions feature to make the software installers execute the malicious scripts," Cisco Talos researcher Chetan Raghuprasad said in a technical report.

Cybercriminals are leveraging a legitimate Windows tool called 'Advanced Installer' to infect the computers of graphic designers with cryptocurrency miners. The attackers promote installers for popular 3D modeling and graphic design software such as Adobe Illustrator, Autodesk 3ds Max, and SketchUp Pro, likely through black hat search engine optimization techniques.

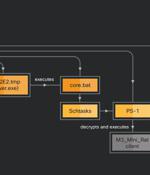
Json from CRED FILE NAMES file name array to GCLOUD CREDS FILES file name array[+] added netrc, kubeconfig, adc. Db from CRED FILE NAMES file name array[-] removed dload function[+] added commented dload function invocation for posting final results[+] added commented wget command to download and execute https://everlost.
Exposed Kubernetes clusters are being exploited by malicious actors to deploy cryptocurrency miners and other backdoors. Cloud security firm Aqua, in a report shared with The Hacker News, said a majority of the clusters belonged to small to medium-sized organizations, with a smaller subset tied to bigger companies, spanning financial, aerospace, automotive, industrial, and security sectors.

Misconfigured and poorly secured Apache Tomcat servers are being targeted as part of a new campaign designed to deliver the Mirai botnet malware and cryptocurrency miners. The findings come...

Poorly managed Linux SSH servers are getting compromised by unknown attackers and instructed to engage in DDoS attacks while simultaneously mining cryptocurrency in the background. "The source code of Tsunami is publicly available so it is used by a multitude of threat actors. Among its various uses, it is mostly used in attacks against IoT devices. Of course, it is also consistently used to target Linux servers," researchers with AhnLab's Security Emergency response Center explained.

Once they've broken into a victims' compute environment - often via compromised credentials - they keep quiet, deploying mining malware and then raking in cryptocurrencies using the stolen compute resources. Plus, according to security researchers, illicit mining is on the rise.

If you're running an Apache NiFi instance exposed on the internet and you have not secured access to it, the underlying host may already be covertly cryptomining on someone else's behalf. "Routers make bad cryptomining servers. Cryptomining may be what they end up doing if the lateral movement doesn't get them anywhere."

A financially motivated threat actor of Indonesian origin has been observed leveraging Amazon Web Services Elastic Compute Cloud instances to carry out illicit crypto mining operations. Cloud security company's Permiso P0 Labs, which first detected the group in November 2021, has assigned it the moniker GUI-vil.