Security News

Over 400 distinct cloud applications delivered malware in 2022, nearly triple the amount seen in the prior year, and 30% of all cloud malware downloads in 2022 originated from Microsoft OneDrive, according to Netskope. "Attackers are increasingly abusing business-critical cloud apps to deliver malware by bypassing inadequate security controls," said Ray Canzanese, Threat Research Director, Netskope Threat Labs.

Business software provider Zoho has urged customers to patch a critical security flaw affecting multiple ManageEngine products."We identified a SQL injection vulnerability in our internal framework that would grant all [.] users unauthenticated access to the backend database," Zoho said.

Synology has released security updates to address a critical flaw impacting VPN Plus Server that could be exploited to take over affected systems.Tracked as CVE-2022-43931, the vulnerability carries a maximum severity rating of 10 on the CVSS scale and has been described as an out-of-bounds write bug in the remote desktop functionality in Synology VPN Plus Server.

Thousands of Citrix Application Delivery Controller and Gateway endpoints remain vulnerable to two critical security flaws disclosed by the company over the last few months. Citrix and the U.S. National Security Agency, earlier this month, warned that CVE-2022-27518 is being actively exploited in the wild by threat actors, including the China-linked APT5 state-sponsored group.

ZDI doesn't just deal in competitive bug hunting in its twice-a-year contests, so it also regularly puts out vulnerability notices for zero-days that were disclosed in more conventional ways, like this one, entitled Linux Kernel ksmbd Use-After-Free Remote Code Execution Vulnerability. Even though this bug has had some dramatic coverage over the holiday weekend, given that it was a remote code execution hole in the Linux kernel itself, and came with a so-called CVSS score of 10/10, considered Critical.

A critical vulnerability in the Ghost CMS newsletter subscription system could allow external users to create newsletters or modify existing ones so that they contain malicious JavaScript. [...]

Multiple high-severity vulnerabilities have been disclosed in Passwordstate password management solution that could be exploited by an unauthenticated remote adversary to obtain a user's plaintext passwords. "Successful exploitation allows an unauthenticated attacker to exfiltrate passwords from an instance, overwrite all stored passwords within the database, or elevate their privileges within the application," Swiss cybersecurity firm modzero AG said in a report published this week.

A critical code-execution vulnerability in Microsoft Windows was patched in September. Like EternalBlue, CVE-2022-37958, as the latest vulnerability is tracked, allows attackers to execute malicious code with no authentication required.
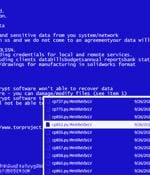
A Rust variant of a ransomware strain known as Agenda has been observed in the wild, making it the latest malware to adopt the cross-platform programming language after BlackCat, Hive, Luna, and RansomExx. A previous version of the ransomware, written in Go and customized for each victim, singled out healthcare and education sectors in countries like Indonesia, Saudi Arabia, South Africa, and Thailand.

Microsoft has revised the severity of a security vulnerability it originally patched in September 2022, upgrading it to "Critical" after it emerged that it could be exploited to achieve remote code execution. Tracked as CVE-2022-37958, the flaw was previously described as an information disclosure vulnerability in SPNEGO Extended Negotiation Security Mechanism.