Security News

Citrix has released security updates for a high-severity security flaw impacting NetScaler Console (formerly NetScaler ADM) and NetScaler Agent that could lead to privilege escalation under...

Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Veeam plugs serious holes in Service Provider Console (CVE-2024-42448, CVE-2024-42449) Veeam has...

Veeam has released security updates to address a critical flaw impacting Service Provider Console (VSPC) that could pave the way for remote code execution on susceptible instances. The...

Veeam released security updates today to address two Service Provider Console (VSPC) vulnerabilities, including a critical remote code execution (RCE) discovered during internal testing. [...]

Veeam has fixed two vulnerabilities in Veeam Service Provider Console (VSPC), one of which (CVE-2024-42448) may allow remote attackers to achieve code exection on the VSPC server machine. The...

In this Help Net Security interview, security researchers Specter and ChendoChap discuss gaming consoles’ unique security model, highlighting how it differs from other consumer devices. They also...
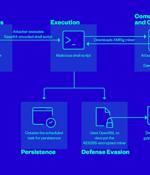
Cybersecurity researchers have found that it's possible for attackers to weaponize improperly configured Jenkins Script Console instances to further criminal activities such as cryptocurrency mining. Jenkins, a popular continuous integration and continuous delivery platform, features a Groovy script console that allows users to run arbitrary Groovy scripts within the Jenkins controller runtime.
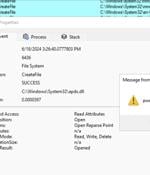
Threat actors are exploiting a novel attack technique in the wild that leverages specially crafted management saved console (MSC) files to gain full code execution using Microsoft Management...

Cloud Console Cartographer is an open-source tool that maps noisy log activity into highly consolidated, succinct events to help security practitioners cut through the noise and understand console behavior in their environment. "Infrastructure as code has replaced a lot of the need for console access for many organizations, but there are still plenty of instances where the console is still being used, and in some cases, you need to use the AWS console to perform certain actions. Cloud Console Cartographer cuts through the noise generated in logs by those console sessions," Daniel Bohannon, Permiso's Principal Threat Researcher, told Help Net Security.
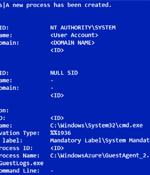
A financially motivated cyber actor has been observed abusing Microsoft Azure Serial Console on virtual machines to install third-party remote management tools within compromised environments. "This method of attack was unique in that it avoided many of the traditional detection methods employed within Azure and provided the attacker with full administrative access to the VM," the threat intelligence firm said.