Security News

Scout Suite is an open-source, multi-cloud security auditing tool designed to assess the security posture of cloud environments. By leveraging the APIs provided by cloud vendors, Scout Suite collects and organizes configuration data, making it easier to identify potential risks.

Traditional cloud security issues often associated with cloud service providers are continuing to decrease in importance, according to the Top Threats to Cloud Computing 2024 report by the Cloud Security Alliance. "It's tempting to think that the reason the same issues have remained in the top spots since the report was last issued stems from a lack of progress in securing these features. The larger picture speaks to the importance placed on these vulnerabilities by organizations and the degrees to which they are working to build ever more secure and resilient cloud environments," said Michael Roza, co-chair, Top Threats Working Group.

Black Hat State-sponsored cyber spies and criminals are increasingly using legitimate cloud services to attack their victims, according to Symantec's threat hunters who have spotted three such operations over recent months, plus new data theft and other malware tools in development by these goons. This piece of malware used Microsoft's Graph API to communicate with the attacker's command and control server, hosted on Microsoft OneDrive.

Users in Russia have been the target of a previously undocumented Android post-compromise spyware called LianSpy since at least 2021. Cybersecurity vendor Kaspersky, which discovered the malware in March 2024, noted its use of Yandex Cloud, a Russian cloud service, for command-and-control communications as a way to avoid having a dedicated infrastructure and evade detection.
Cloud computing certifications can expand your skills and teach you how to navigate major cloud providers like Google Cloud or AWS. Specializations in certain cloud providers can serve as strong foundations for niche careers, while nearly all businesses use some form of cloud service. These courses teach how to perform cloud support in Microsoft Azure solutions and services, and how to adapt technology diagnostic skills specifically to IT and cloud problems.

More organizations rely on cloud platforms to reap the benefits of scalability, flexibility, availability, and reduced costs. However, cloud environments come with security challenges and...

Cloud GenAI workloads inherit pre-existing cloud security challenges, and security teams must proactively evolve innovative security countermeasures, including threat detection mechanisms. More recently, detection engineering has spun off as a specialized aspect of threat detection, allowing detection engineers to customize threat detection systems.

Cirrus is an open-source Python-based tool designed to streamline Google Cloud forensic evidence collection. It can streamline environment access and evidence collection in investigations involving Google Workspace and GCP. The tool simplifies incident response activities and enhances an organization's security posture.
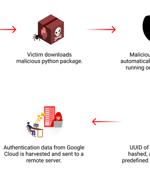
Cybersecurity researchers have discovered a malicious package on the Python Package Index repository that targets Apple macOS systems with the goal of stealing users' Google Cloud credentials from a narrow pool of victims. The package, named "Lr-utils-lib," attracted a total of 59 downloads before it was taken down.
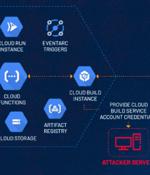
Cybersecurity researchers have disclosed a privilege escalation vulnerability impacting Google Cloud Platform's Cloud Functions service that an attacker could exploit to access other services and sensitive data in an unauthorized manner. "An attacker could escalate their privileges to the Default Cloud Build Service Account and access numerous services such as Cloud Build, storage, artifact registry and container registry," the exposure management company said in a statement.