Security News

The infamous cryptojacking group known as TeamTNT appears to be readying for a new large-scale campaign targeting cloud-native environments for mining cryptocurrencies and renting out breached...

Also updates bug bounty program with $1M payout In June, Apple used its Worldwide Developer Conference to announce the creation of the Private Cloud Compute platform to run its AI Intelligence...

Apple has publicly made available its Private Cloud Compute (PCC) Virtual Research Environment (VRE), allowing the research community to inspect and verify the privacy and security guarantees of...

Apple created a Virtual Research Environment to allow public access to testing the security of its Private Cloud Compute system, and released the source code for some "key components" to help...

Remember Bucket Monopoly? Yeah, it gets worse Amazon Web Services has fixed a flaw in its open source Cloud Development Kit that, under the right conditions, could allow an attacker to hijack a...
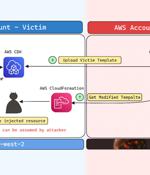
Cybersecurity researchers have disclosed a security flaw impacting Amazon Web Services (AWS) Cloud Development Kit (CDK) that could have resulted in an account takeover under specific...

Recently, IBM X-Force released its 2024 Cloud Threat Landscape Report. This uses incident data and insights to reveal how attackers successfully compromise organizations by leveraging...

Cybersecurity researchers have discovered severe cryptographic issues in various end-to-end encrypted (E2EE) cloud storage platforms that could be exploited to leak sensitive data. "The...

Several end-to-end encrypted (E2EE) cloud storage platforms are vulnerable to a set of security issues that could expose user data to malicious actors. [...]

Microsoft has lost several weeks of cloud security logs that its customers rely on to spot cyber intrusions. What happened As reported by Business Insider earlier this month, Microsoft privately...