Security News

China-based hackers known to target US defense and software companies are now targeting organizations using a vulnerability in the SolarWinds Serv-U FTP server. Today, SolarWinds released a security update for a zero-day vulnerability in Serv-U FTP servers that allow remote code execution when SSH is enabled.
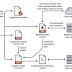
Cybersecurity researchers are warning about a new malware that's striking online gambling companies in China via a watering hole attack to deploy either Cobalt Strike beacons or a previously undocumented Python-based backdoor called BIOPASS RAT that takes advantage of Open Broadcaster Software Studio's live-streaming app to capture the screen of its victims to attackers. The attack involves deceiving gaming website visitors into downloading a malware loader camouflaged as a legitimate installer for popular-but-deprecated apps such as Adobe Flash Player or Microsoft Silverlight, only for the loader to act as a conduit for fetching next-stage payloads.

A string of cyber espionage campaigns dating all the way back to 2014 and likely focused on gathering defense information from neighbouring countries have been linked to a Chinese military-intelligence apparatus. In a wide-ranging report published by Massachusetts-headquartered Recorded Future this week, the cybersecurity firm's Insikt Group said it identified ties between a group it tracks as "RedFoxtrot" to the People's Liberation Army Unit 69010 operating out of Ürümqi, the capital of the Xinjiang Uyghur Autonomous Region in the country.

A cyberespionage campaign blamed on China was more sweeping than previously known, with suspected state-backed hackers exploiting a device meant to boost internet security to penetrate the computers of critical U.S. entities. The Pulse Secure hack has largely gone unnoticed while a series of headline-grabbing ransomware attacks have highlighted the cyber vulnerabilities to U.S. critical infrastructure, including one on a major fuels pipeline that prompted widespread shortages at gas stations.

The cyber assault on Air India that came to light last month lasted for a period of at least two months and 26 days, new research has revealed, which attributed the incident with moderate confidence to a Chinese nation-state threat actor called APT41. On May 21, India's flag carrier airline, Air India, disclosed a data breach affecting 4.5 million of its customers over a period stretching nearly 10 years in the wake of a supply chain attack directed at its Passenger Service System provider SITA earlier this February.

The cyberattack on SITA that impacted multiple airlines around the world was orchestrated by a Chinese nation-state threat actor tracked as APT41, security researchers at detection and prevention firm Group-IB say. Air India revealed that the attack was related to SITA PSS, which processes personally identifiable information.

An advanced persistent threat that Russia found inside government systems was too crude to have been the work of a Western nation, says security researcher Juan Andrés Guerrero-Saade of Sentinel Labs, before suggesting the malware came from a Chinese entity. Russian telco and IT services provider Rostelecom and the nation's National Coordination Center for Computer Incidents, an arm of the Russian Federal Security Service, in May published a joint report that detailed their assessment of attacks on several Russian government entities detected in 2020.

Researchers said, is the novel backdoor, which they said has been in development by a Chinese APT for at least three years. A multi-stage chain eventually results in the installation of the backdoor module, which is called "Victory." It "Appears to be a custom and unique malware," according to Check Point.

USENIX, the not-for-profit advanced computing association, has decided to put an end to its beloved LISA sysadmin conferences, at least as a standalone event. In an online announcement, the LISA steering committee said that after 35 years of producing the "Best systems engineering content" the event "Will no longer be scheduled as a standalone conference."
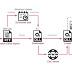
The infection chain works by sending decoy documents, impersonating other entities within the government, to multiple members of the Ministry of Foreign Affairs, which, when opened, retrieves a next-stage payload from the attacker's server that contains an encrypted downloader. The use of weaponized copies of legitimate-looking official documents also suggests that "The attackers first had to attack another department within the targeted state, stealing and weaponizing documents for use against the Ministry of Foreign Affairs," said Lotem Finkelstein, head of threat intelligence at Check Point.