Security News

Apple has recently addressed a vulnerability that lets attackers with root privileges bypass System Integrity Protection to install "Undeletable" malware and access the victim's private data by circumventing Transparency, Consent, and Control security checks. Apple has patched the vulnerability in security updates for macOS Ventura 13.4, macOS Monterey 12.6.6, and macOS Big Sur 11.7.7, released two weeks ago, on May 18.

D-Link has fixed two critical-severity vulnerabilities in its D-View 8 network management suite that could allow remote attackers to bypass authentication and execute arbitrary code.D-View is a network management suite developed by the Taiwanese networking solutions vendor D-Link, used by businesses of all sizes for monitoring performance, controlling device configurations, creating network maps, and generally making network management and administration more efficient and less time-consuming.

CISA warned today of a security vulnerability affecting Samsung devices used in attacks to bypass Android address space layout randomization protection. The exposed info can be used by local attackers with high privileges to conduct an ASLR bypass which could enable the exploitation of memory-management issues.

Microsoft fixed a security vulnerability this week that could be used by remote attackers to bypass recent patches for a critical Outlook zero-day security flaw abused in the wild. "All Windows versions are affected by the vulnerability. As a result, all Outlook client versions on Windows are exploitable," Barnea explained.
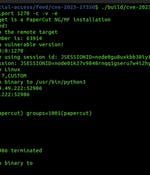
Cybersecurity researchers have found a way to exploit a recently disclosed critical flaw in PaperCut servers in a manner that bypasses all current detections. Tracked as CVE-2023-27350, the issue affects PaperCut MF and NG installations that could be exploited by an unauthenticated attacker to execute arbitrary code with SYSTEM privileges.

Security researchers discovered a new malicious browser extension called Rilide, that targets Chromium-based products like Google Chrome, Brave, Opera, and Microsoft Edge. Researchers at Trustwave SpiderLabs found that Rilide mimicked benign Google Drive extensions to hide in plain sight while abusing built-in Chrome functionalities.

The answer, our researchers discovered, is that so-called active adversaries might be able to shake loose at least some queued-up data from at least least some access points. The researchers figured out various ways of tricking some access points into releasing those queued-up network packets.

Microsoft has released a script to make it easier to patch a BitLocker bypass security vulnerability in the Windows Recovery Environment. This PowerShell script simplifies the process of securing WinRE images against attempts to exploit the CVE-2022-41099 flaw that enables attackers to bypass the BitLocker Device Encryption feature system storage devices.

A new phishing campaign targets organizations in Eastern European countries with the Remcos RAT malware with aid from an old Windows User Account Control bypass discovered over two years ago. The use of mock trusted directories to bypass Windows User Account Control stands out in the attack as it's been known since 2020 but remains effective today.

BlackLotus, a UEFI bootkit that's sold on hacking forums for about $5,000, can now bypass Secure Boot, making it the first known malware to run on Windows systems even with the firmware security feature enabled. Secure Boot is supposed to prevent devices from running unauthorized software on Microsoft machines.