Security News

Security teams can no longer afford to treat third-party security as a compliance checkbox, according to SecurityScorecard. Traditional vendor risk assessments, conducted annually or quarterly,...

Cyber threats don't show up one at a time anymore. They’re layered, planned, and often stay hidden until it’s too late. For cybersecurity teams, the key isn’t just reacting to alerts—it’s spotting...

It wasn't ransomware headlines or zero-day exploits that stood out most in this year's Verizon 2025 Data Breach Investigations Report (DBIR) — it was what fueled them. Quietly, yet consistently,...

Data breaches played a key role in significant financial losses faced by consumers due to fraud. In this Help Net Security video, Steve Yin, Global Head of Fraud at TransUnion, and Brad...

What happens when cybercriminals no longer need deep skills to breach your defenses? Today’s attackers are armed with powerful tools that do the heavy lifting — from AI-powered phishing kits to...

Not every security vulnerability is high risk on its own - but in the hands of an advanced attacker, even small weaknesses can escalate into major breaches. These five real vulnerabilities,...

The FBI has asked the public for information on Chinese Salt Typhoon hackers behind widespread breaches of telecommunications providers in the United States and worldwide. [...]
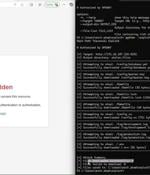
Cybersecurity researchers have disclosed three security flaws in the Rack Ruby web server interface that, if successfully exploited, could enable attackers to gain unauthorized access to files,...

Cybercriminals are targeting software shops, accountants, lawyers The percentage of confirmed data breaches involving third-party relationships doubled last year as cybercriminals increasingly...

The exploitation of vulnerabilities has seen another year of growth as an initial access vector for breaches, reaching 20%, according to Verizon’s 2025 Data Breach Investigations Report....