Security News

Hanko is an open-source, API-first authentication solution purpose-built for the passwordless era. “We focus on helping developers and organizations modernize their authentication flows by...

Email is still the top way attackers get into organizations. Now, big players like Google, Yahoo, and Microsoft are cracking down. They’re starting to require email authentication, specifically...

By now, most CISOs agree: passwords are the weakest link in the authentication chain. They’re easy to guess, hard to manage, and constantly reused. Even the most complex password policies don’t...

CVE-2025-22230 is described as an "authentication bypass vulnerability" by Broadcom, allowing hackers to perform high-privilege operations without the necessary credentials.

Broadcom released security updates today to fix a high-severity authentication bypass vulnerability in VMware Tools for Windows. [...]
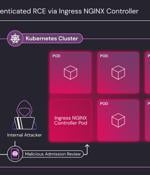
A set of five critical security shortcomings have been disclosed in the Ingress NGINX Controller for Kubernetes that could result in unauthenticated remote code execution, putting over 6,500...

GitLab released security updates for Community Edition (CE) and Enterprise Edition (EE), fixing nine vulnerabilities, among which two critical severity ruby-saml library authentication bypass flaws. [...]

Taiwanese company Moxa has released a security update to address a critical security flaw impacting its PT switches that could permit an attacker to bypass authentication guarantees. The...

Rubrik disclosed last month that one of its servers hosting log files was breached, causing the company to rotate potentially leaked authentication keys. [...]

Microsoft has fixed an issue that caused Entra ID DNS authentication failures when using the company's Seamless SSO and Microsoft Entra Connect Sync. [...]