Security News

A vulnerability dubbed "CosmicSting" impacting Adobe Commerce and Magento websites remains largely unpatched nine days after the security update has been made available, leaving millions of sites open to catastrophic attacks. "CosmicSting is the worst bug to hit Magento and Adobe Commerce stores in two years," says Sansec.

The Federal Trade Commission has filed a complaint in US federal court against Adobe and two executives, Maninder Sawhney and David Wadhwani, for deceptive practices related to their subscription plans. Defendants Sawhney, Senior Vice President of Digital Go To Market & Sales at Adobe, and Wadhwani, President of Digital Media Business at Adobe, are accused of knowing about these violations yet continuing the same unlawful practices.

Security researchers in Adobe's bug bounty program can now pick up rewards for finding vulnerabilities in Adobe Firefly and Content Credentials. Members of Adobe's public bug bounty program will be eligible to work with Adobe Firefly and Content Credentials in the second half of 2024, and applications for the private program are open.
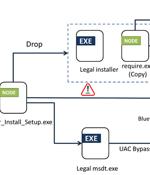
Bogus installers for Adobe Acrobat Reader are being used to distribute a new multi-functional malware dubbed Byakugan. The starting point of the attack is a PDF file written in Portuguese that,...

One of the variants observed uses on Windows a fake installer for an Adobe product to trick the user into deploying the malware. Sophos' Advanced Threat Response Joint Task Force, or Sophos X-Ops for short, noticed fresh Qbot activity recently, with up to 10 new malware builds emerging since mid-December.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added six security flaws to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence of active exploitation. This...

Patch Tuesday Microsoft rang in the New Year with a relatively calm Patch Tuesday: Just 49 Windows security updates including fixes for two critical-rated bugs, plus four high-severity Chrome flaws in Microsoft Edge. "And while it's listed as exploitation less likely, because Hyper-V runs as the highest privileges in a computer, it is worth thinking about patching," Ben McCarthy, lead cyber security engineer at Immersive Labs told The Register.

Unknown attackers have leveraged a critical vulnerability in the Adobe ColdFusion application development platform to access government servers, the Cybersecurity and Infrastructure Security Agency has shared. Adobe disclosed and fixed the flaw in mid-March 2023, and said that it was "Aware that CVE-2023-26360 has been exploited in the wild in very limited attacks".

The U.S. Cybersecurity and Infrastructure Security Agency is warning about hackers actively exploiting a critical vulnerability in Adobe ColdFusion identified as CVE-2023-26360 to gain initial access to government servers. The security issue allows executing arbitrary code on servers running Adobe ColdFusion 2018 Update 15 and older, and 2021 Update 5 and earlier.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday added a high-severity flaw in Adobe Acrobat Reader to its Known Exploited Vulnerabilities (KEV) catalog, citing evidence...