Security News > 2024 > April

The MITRE Corporation says that a state-backed hacking group breached its systems in January 2024 by chaining two Ivanti VPN zero-days. The incident was discovered after suspicious activity was detected on MITRE's Networked Experimentation, Research, and Virtualization Environment, an unclassified collaborative network used for research and development.

The researchers used an approach dubbed 'blind quantum computing' to connect two quantum computing entities; this simulates the situation where an employee at home or in an office remotely connects to a quantum server via the cloud. Professor David Lucas, the co-head of the Oxford University Physics research team, said in a press release: "We have shown for the first time that quantum computing in the cloud can be accessed in a scalable, practical way which will also give people complete security and privacy of data, plus the ability to verify its authenticity."

The United Nations Development Programme is investigating a cyberattack after threat actors breached its IT systems to steal human resources data. While the UN agency has yet to link the attack to a specific threat group, the 8Base ransomware gang added a new UNDP entry to its dark web data leak website on March 27.

Approximately 22,500 exposed Palo Alto GlobalProtect firewall devices are likely vulnerable to the CVE-2024-3400 flaw, a critical command injection vulnerability that has been actively exploited in attacks since at least March 26, 2024. CVE-2024-3400 is a critical vulnerability impacting specific Palo Alto Networks' PAN-OS versions in the GlobalProtect feature that allows unauthenticated attackers to execute commands with root privileges using command injection triggered by arbitrary file creation.

Advertising presented to you on this service can be based on limited data, such as the website or app you are using, your non-precise location, your device type or which content you are interacting with. Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests.
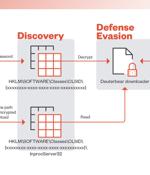
Technology, research, and government sectors in the Asia-Pacific region have been targeted by a threat actor called BlackTech as part of a recent cyber attack wave. The intrusions pave the way for...

More organizations hit by ransomware gangs are starting to realize that it doesn't pay to pay up: "In Q1 2024, the proportion of victims that chose to pay touched a new record low of 28%," ransomware incident response firm Coveware has found. "LockBit was found to still be holding the stolen data of victims that had paid a ransom, and we have also seen prior Hive victims that had paid the extortion, have their data posted on the Hunters International leak site," the company said, noting that "Future victims of data exfiltration extortion are getting more evidence daily that payments to suppress leaks have little efficacy in the short and long term."

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.
Attackers are increasingly making use of “networkless” attack techniques targeting cloud apps and identities. Here’s how attackers can (and are) compromising organizations – without ever needing...

Threat actors behind the Akira ransomware group have extorted approximately $42 million in illicit proceeds after breaching the networks of more than 250 victims as of January 1, 2024. "Since...