Security News > 2023 > July

Chinese companies, including state-owned defense companies, are evading tech sanctions and fueling Moscow's war in Ukraine, according to a US report released on Thursday. "Beijing is pursuing a variety of economic support mechanisms for Russia that mitigate both the impact of Western sanctions and export controls," states the report.

Security experts from HackerOne and beyond weigh in on malicious prompt engineering and other attacks that could strike through LLMs. HackerOne, a security platform and hacker community forum, hosted a roundtable on Thursday, July 27, about the way generative artificial intelligence will change the practice of cybersecurity. How threat actors take advantage of generative AI. "We have to remember that systems like GPT models don't create new things - what they do is reorient stuff that already exists stuff it's already been trained on," said Klondike.

Microsoft Edge web browser has been displaying security warnings after Twitter changed its name to 'X'. Amid its rapid rebranding over the last few days, Twitter has also ditched the famed bird icon for a Unicode character which resembles the letter X but infact bears Mathematical meaning. Microsoft Edge warns this is a potential security issue-and it's working as intended.

CISA warned today of the significant breach risks linked to insecure direct object reference vulnerabilities impacting web applications in a joint advisory with the Australian Cyber Security Centre and U.S. National Security Agency. IDOR vulnerabilities are flaws in web apps that enable attackers to access and manipulate sensitive data by directly referencing internal objects or resources.

Two new Android malware families named 'CherryBlos' and 'FakeTrade' were discovered on Google Play, aiming to steal cryptocurrency credentials and funds or conduct scams. The malicious apps use various distribution channels, including social media, phishing sites, and deceitful shopping apps on Google Play, Android's official app store.

The Hawaiʻi Community College has admitted that it paid a ransom to ransomware actors to prevent the leaking of stolen data of approximately 28,000 people. On June 19th, 2023, the relatively new NoEscape ransomware gang listed UH on its extortion portal, threatening to publish 65 GB of stolen data in a week if a ransom was not paid.

The threat actors linked to the malware loader known as IcedID have made updates to the BackConnect module that's used for post-compromise activity on hacked systems, new findings from Team Cymru reveal. "For the past several months, BackConnect traffic caused by IcedID was easy to detect because it occurred over TCP port 8080," Palo Alto Networks Unit 42 said in late May 2023.
An ongoing cyber attack campaign has set its sights on Korean-speaking individuals by employing U.S. Military-themed document lures to trick them into running malware on compromised systems. Cybersecurity firm Securonix is tracking the activity under the name STARK#MULE. "Based on the source and likely targets, these types of attacks are on par with past attacks stemming from typical North Korean groups such as APT37 as South Korea has historically been a primary target of the group, especially its government officials," security researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in a report shared with The Hacker News.

What we found is an attack scenario that results from chaining security issues found on different Porsche's assets, a website and a GraphQL API, that could lead to data exfiltration. Typically, to be able to perpetrate a CSRF attack from an attacker's-controlled website the victims' web browsers must automatically include the jwtToken cookie in the API requests.
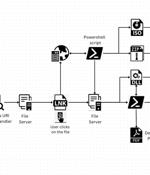
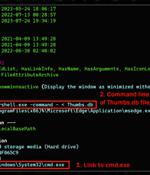
A legitimate Windows search feature is being exploited by malicious actors to download arbitrary payloads from remote servers and compromise targeted systems with remote access trojans such as AsyncRAT and Remcos RAT. The novel attack technique, per Trellix, takes advantage of the "Search-ms:" URI protocol handler, which offers the ability for applications and HTML links to launch custom local searches on a device, and the "Search:" application protocol, a mechanism for calling the desktop search application on Windows. It's worth noting that clicking on the link also generates a warning "Open Windows Explorer?," approving which "The search results of remotely hosted malicious shortcut files are displayed in Windows Explorer disguised as PDFs or other trusted icons, just like local search results," the researchers explained.