Security News > 2023 > April

Within the largest financial institutions, insurers, and retailers, the rise and adoption of AI, an impending recession, and the return of pre-pandemic fraud techniques are driving record rates of fraud attacks for consumers and enterprises alike, according to Pindrop. "In addition to new technologies, fraudsters are reverting to pre-pandemic social engineering tricks, causing retailers and financial institutions billions in losses. While this report highlights the dangers of today's fraud landscape, we are proud to partner with several of the largest financial institutions globally in order to safeguard their assets and protect them from fraud," Balasubramanian continued.

How to create Portainer teams for restricted development access Jack Wallen shows you how to create a team and add users in Portainer in a secure way. With Teams, you can create multiple teams, add users and then create containers with restricted access to only the teams who need to manage specific deployments.

LockBit has developed ransomware that can encrypt files on Arm-powered Macs, said to be a first for the prolific cybercrime crew. "As much as I can tell, this is the first Apple's Mac devices targeting build of LockBit ransomware sample seen," MHT tweeted over the weekend.

Ex-Conti ransomware members have teamed up with the FIN7 threat actors to distribute a new malware family named 'Domino' in attacks on corporate networks. Domino is a relatively new malware family consisting of two components, a backdoor named 'Domino Backdoor,' which in turn drops a 'Domino Loader' that injects an info-stealing malware DLL into the memory of another process.

If you plug your phone into a USB outlet that's provided by someone else, how can you be sure that it's only providing charging power, and not secretly trying to negotiate a data connection with your device at the same time? In the words of the FCC:. If your battery is running low, be aware that juicing up your electronic device at free USB port charging stations, such as those found in airports and hotel lobbies, might have unfortunate consequences.

The Chinese state-sponsored hacking group APT41 was found abusing the GC2 red teaming tool in data theft attacks against a Taiwanese media and an Italian job search company. In Google's April 2023 Threat Horizons Report, released last Friday, security researchers in its Threat Analysis Group revealed that APT41 was abusing the GC2 red teaming tool in attacks.

Israeli spyware vendor QuaDream is allegedly shutting down its operations in the coming days, less than a week after its hacking toolset was exposed by Citizen Lab and Microsoft. The company's board of directors are looking to sell off its intellectual property, the report further added.
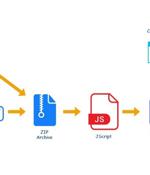
A new QBot malware campaign is leveraging hijacked business correspondence to trick unsuspecting victims into installing the malware, new findings from Kaspersky reveal. QBot is a banking trojan that's known to be active since at least 2007.

Legion targets various services for email exploitation, according to Cado, whose research indicates that Legion is likely linked to the AndroxGh0st malware family first reported in December 2022. The report said Legion appears to be part of an emerging generation of hacking tools that aim to automate the credential harvesting process to compromise SMTP services.
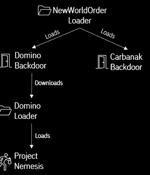
A new strain of malware developed by threat actors likely affiliated with the FIN7 cybercrime group has been put to use by the members of the now-defunct Conti ransomware gang, indicating collaboration between the two crews. The latest intrusion wave, spotted by IBM Security X-Force two months ago, involves the use of Dave Loader, a crypter previously attributed to the Conti group, to deploy the Domino backdoor.