Security News > 2020 > April

In a blunder described as "Astonishing and worrying," Sheffield City Council's automatic number-plate recognition system exposed to the internet 8.6 million records of road journeys made by thousands of people, The Register can reveal. The ANPR camera system's internal management dashboard could be accessed by simply entering its IP address into a web browser.
Germany on Sunday pulled an about-face regarding the best way to use smart phones to trace people's contacts with those infected by COVID-19, embracing a decentralized Bluetooth-based approach instead of the more invasive location tracking proposed in other approaches. Apple and Google first announced their contact tracing collaboration two weeks ago, on 10 April.

Learn more about what Maor's investigations into underground forums have revealed about how credentials are being uncovered, shared and leveraged to attack remote workers, in this week's Threatpost podcast. Now, a few weeks back, you had found that there were more than 2,000 compromised Zoom credentials that were missing being shared on underground forums.

Microsoft has quickly fixed a flaw in its Teams videoconferencing and collaboration program that could have allowed attackers to launch a wormlike attack on multiple accounts by sending one victim a malicious GIF image. If an attacker can somehow force a user to visit the sub-domains that have been taken over, the victim's browser will send this cookie to the attacker's server and the attacker can create a skype token.

Example CEO and Management Board Meeting for all staffs on Zoom Meeting This is a reminder that your zoom meeting appointment with H.R and Audit Head will start in few minutes. Your presence is crucial to this meeting and equally required to commence this Q1 perfomance review meeting Join this Live Meeting Meeting Purpose: Contract Suspension / Termination Trial.

A study of vulnerabilities - bugs that can be a gateway for malware or allow privilege escalation by an intruder - shows that Windows platforms have the most by far, but that they also tend to be fixed quickly, compared to Linux systems or appliances like routers, printers and scanners. The assets analysed mostly exclude mobile devices, leaving the top five most common platforms as Windows 10, Linux, Cisco, Windows 7 and Windows 2012.

The UK has decided to break with growing international consensus and insist its upcoming coronavirus contact-tracing app is run through centralised British servers - rather than follow the decentralized Apple-Google approach. Within the details over how it would work, the memo revealed the NHS and UK government reckon the contact-tracing protocols built by Apple and Google protect user privacy under advisement only.

As a provider of cyber insurance, we have the misfortune of responding to ransomware attacks across tens of thousands of organizations, and the trends are worrying. Although the majority of ransomware campaigns were observed to target Windows environments, there were also successful attacks against Linux environments.
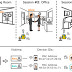
Researchers have uncovered a potential means to profile and track online users using a novel approach that combines device identifiers with their biometric information. The details come from a newly published research titled "Nowhere to Hide: Cross-modal Identity Leakage between Biometrics and Devices" by a group of academics from the University of Liverpool, New York University, The Chinese University of Hong Kong, and University at Buffalo SUNY. "Prior studies on identity theft only consider the attack goal for a single type of identity, either for device IDs or biometrics," Chris Xiaoxuan Lu, Assistant Professor at the University of Liverpool, told The Hacker News in an email interview.

Researchers have uncovered a potential means to profile and track online users using a novel approach that combines device identifiers with their biometric information. The details come from a newly published research titled "Nowhere to Hide: Cross-modal Identity Leakage between Biometrics and Devices" by a group of academics from the University of Liverpool, New York University, The Chinese University of Hong Kong, and University at Buffalo SUNY. "Prior studies on identity theft only consider the attack goal for a single type of identity, either for device IDs or biometrics," Chris Xiaoxuan Lu, Assistant Professor at the University of Liverpool, told The Hacker News in an email interview.