Security News

Apple has patched two zero-day vulnerabilities exploited to deliver NSO Group's Pegasus spyware."The exploit chain was capable of compromising iPhones running the latest version of iOS without any interaction from the victim," Citizen Lab shared.

Apple released emergency security updates to fix two new zero-day vulnerabilities exploited in attacks targeting iPhone and Mac users, for a total of 13 exploited zero-days patched since the start of the year. Since the start of the year, Apple has patched 13 zero-day bugs exploited in attacks against devices running iOS, macOS, iPadOS, and watchOS. While Apple has yet to disclose details regarding attacks exploiting the flaws patched today, it acknowledged that CVE-2023-41064 was found and reported by Citizen Labs, whose researchers have previously shared information on other Apple zero-days exploited to deploy commercial spyware on computers and iPhones in targeted attacks.

Google's Threat Analysis Group says North Korean state hackers are again targeting security researchers in attacks using at least one zero-day in an undisclosed popular software. Researchers attacked in this campaign are involved in vulnerability research and development, according to Google's team of security experts that protects the company's users from state-sponsored attacks.

The September 2023 Android security updates tackle 33 vulnerabilities, including a zero-day bug currently targeted in the wild. "Exploitation for many issues on Android is made more difficult by enhancements in newer versions of the Android platform. We encourage all users to update to the latest version of Android where possible."

Google has rolled out monthly security patches for Android to address a number of flaws, including a zero-day bug that it said may have been exploited in the wild. Tracked as CVE-2023-35674, the high-severity vulnerability is described as a case of privilege escalation impacting the Android Framework.

An Atlas VPN zero-day vulnerability affecting the Linux client leaks a user's real IP address simply by visiting a website. Atlas VPN is a VPN product that offers a cost-effective solution based on WireGuard and supports all major operating systems.

Atlas VPN has confirmed the existence of a zero-day vulnerability that may allow website owners to discover Linux users' real IP address. Details about this zero-day vulnerability as well as exploit code have been publicly released on Reddit several days ago by the person who discovered the flaw and purportedly first tried to privately share the discovery with Atlas VPN. About the Atlas VPN zero-day vulnerability.

We introduce Silverfort Unified Identity Protection, a comprehensive solution that offers enhanced security for AD environments against the misuse of compromised credentials. AD environments are highly vulnerable to attacks that make use of compromised credentials.
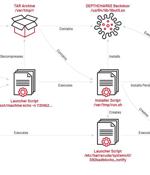
A suspected Chinese-nexus hacking group exploited a recently disclosed zero-day flaw in Barracuda Networks Email Security Gateway appliances to breach government, military, defense and aerospace, high-tech industry, and telecom sectors as part of a global espionage campaign. What's more, FOXTROT shares overlaps with an open-source rootkit called Reptile, which has been extensively used by multiple Chinese hacking crews in recent months.

Suspected Chinese hackers disproportionately targeted and breached government and government-linked organizations worldwide in recent attacks targeting a Barracuda Email Security Gateway zero-day, with a focus on entities across the Americas. Barracuda warned customers that the vulnerability was being exploited to breach ESG appliances on May 20, when it also patched all vulnerable devices remotely.