Security News

The three reports link the most prominent security trends and paint an accurate map of the modern attack landscape. An up-to-date analysis of ransomware attack trends highlight the risks and suggest mitigation, while an analysis of Web app and API attack trends offers a fresh look at the infection vectors used by ransomware operators and others.

US law enforcement has shut down another dark web market, seizing and dismantling SSNDOB, a site dealing in stolen personal information. Prior to the takedown, SSNDOB reportedly had 24 million individuals' records available for purchase, which it regularly advertised on dark web forums.

In a joint advisory [PDF] this week, the FBI, CISA and US Treasury Department outlined technical details about how Karakurt operates, along with actions to take, indicators of compromise, and sample ransom notes. Karakurt doesn't target any specific sectors or industries, and the gang's victims haven't had any of their documents encrypted and held to ransom.

The U.S. Department of Justice on Wednesday announced the seizure of three domains used by cybercriminals to trade stolen personal information and facilitate distributed denial-of-service attacks for hire. The former of which allowed its users to traffic hacked personal data and offered a searchable database containing illegally amassed information obtained from over 10,000 data breaches.

A rapidly evolving IoT malware dubbed "EnemyBot" is targeting content management systems, web servers and Android devices. The Alien lab research team study found four main sections of the malware.
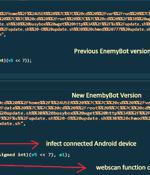
A nascent Linux-based botnet named Enemybot has expanded its capabilities to include recently disclosed security vulnerabilities in its arsenal to target web servers, Android devices, and content management systems. "The malware is rapidly adopting one-day vulnerabilities as part of its exploitation capabilities," AT&T Alien Labs said in a technical write-up published last week.
Threat actors behind web skimming campaigns are leveraging malicious JavaScript code that mimics Google Analytics and Meta Pixel scripts in an attempt to sidestep detection. Last year, Malwarebytes disclosed a campaign wherein malicious actors were observed delivering PHP-based web shells embedded within website favicons to load the skimmer code.
A new research published by academics from KU Leuven, Radboud University, and the University of Lausanne has revealed that users' email addresses are exfiltrated to tracking, marketing, and analytics domains before such is submitted and without prior consent. LiveRamp, Taboola, Adobe, Verizon, Yandex, Meta, TikTok, Salesforce, Listrak, and Oracle are some of the top third-party trackers that have been spotted logging email addresses, while Yandex, Mixpanel, and LogRocket lead the list in the password-grabbing category.

The latest variant of the Sysrv botnet malware is menacing Windows and Linux systems with an expanded list of vulnerabilities to exploit, according to Microsoft. The strain, which Microsoft's Security Intelligence team calls Sysrv-K, scans the internet for web servers that have security holes, such as path traversal, remote file disclosure, and arbitrary file download bugs, that can be exploited to infect the machines.
The purpose of website trackers is to monitor visitor activity, derive data points related to preferences, log interactions, and maintain a persistent anonymous ID for each user. The sites use trackers to provide a more personalized online experience to their users, but they also allow third-party trackers to help advertisers serve targeted ads to their visitors and increase monetary gains.