Security News

If an AI breaks the rules for you, does that count as breaking the rules? This is the essential question being taken up by the Federal Election Commission this month, and public input is needed to curtail the potential for AI to take US campaigns off the rails. Future uses of AI by campaigns go far beyond deepfaked images.

US authorities have issued an urgent plea to network admins to patch the critical vulnerability in Atlassian Confluence Data Center and Server amid ongoing nation-state exploitation. "Due to the ease of exploitation, CISA, FBI, and MS-ISAC expect to see widespread exploitation of unpatched Confluence instances in government and private networks."

For years it seemed as though the construction industry was "Immune" to security attacks, according to a research paper [PDF] by the Association of General Construction of America in 2021. Why? "Threat actors know that the construction industry is in some areas behind in data security and privacy initiatives. This is in large part because this industry, to date, avoided heavy regulation in data security and privacy laws. The limited regulation and guidance in the construction industry may have contributed to less focus on cyber security than in other industries."

A US Navy service member pleaded guilty yesterday to receiving thousands of dollars in bribes from a Chinese spymaster in exchange for passing on American military secrets. Petty Officer Wenheng Zhao, 26, aka Thomas Zhao, of Monterey Park, California, now faces up to 20 years in prison for two federal felony offenses: conspiring with a People's Republic of China intelligence officer, and receiving a bribe.

Opinion The UK Extension to the EU-US Data Privacy Framework will enter into force on October 12, allowing certifying entities to easily transfer personal data from the UK to the US. Transferring personal data across the Atlantic would otherwise be prohibited under the UK General Data Protection Regulation without transfer mechanisms. As the UK is no longer a member of the European Union, the DPF does not automatically enable the transfer of personal data from the UK to the US. Transfers of personal data from the UK will require a Data Bridge.
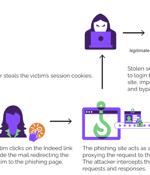
Microsoft, the Dark Web and the name John Malkovich all factor into this EvilProxy phishing attack. A new EvilProxy phishing attack is leveraging an open redirection flaw from the legitimate Indeed.com job search site, according to a report from Menlo Security, a cloud-based security company.

The U.S. Federal Emergency Management Agency and the Federal Communications Commission will run an emergency alert test today to check Emergency Alert System and Wireless Emergency Alerts capabilities nationwide. On consumers' phones, WEA alert messages will read: "This is a test of the National Wireless Emergency Alert System. No action is needed."

The first of two US government prosecutions of former FTX CEO Sam Bankman-Fried commenced in New York on Monday, only a day after the cryptocurrency tycoon sued his own insurance company for failing to cover his legal costs. Who is SBF... Sam Bankman-Fried co-founded cryptocurrency exchange FTX and served as its CEO. He also co-founded Alameda Research, a hedge fund intertwined with FTX. SBF stepped down late last year and has been charged with fraud over allegations FTX and Alameda, among other things, siphoned billions in people's deposits to fund luxury lifestyles, invest in a whole range of businesses, and gamble on digital assets.

Chinese hackers stole tens of thousands of emails from U.S. State Department accounts after breaching Microsoft's cloud-based Exchange email platform in May. During a recent Senate staff briefing, U.S. State Department officials disclosed that the attackers stole at least 60,000 emails from Outlook accounts belonging to State Department officials stationed in East Asia, the Pacific, and Europe, as Reuters first reported. Microsoft did not disclose specific details regarding the affected organizations, government agencies, or countries impacted by this email breach.

Security researcher Sam Curry describes a stressful situation he encountered upon his return to the U.S. when border officials and federal agents seized and searched his electronic devices. Why, you ask? All because his IP address landed in the logs of a crypto wallet associated with a phishing scam that Curry had earlier helped investigate as a part of his job-a scam that the feds were now investigating.