Security News

Multiple regional conflicts, such as Russia’s continued invasion of Ukraine and the Israel-Hamas conflict, have resulted in a surge in cyberattacks and hacktivist activities, according to Trellix....

This month’s roundup features exceptional open-source cybersecurity tools that are gaining attention for strengthening security across various environments. ScubaGear ScubaGear is an open-source...

We hear terms like “state-sponsored attacks” and “critical vulnerabilities” all the time, but what’s really going on behind those words? This week’s cybersecurity news isn’t just about hackers and...
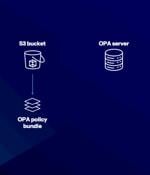
Cybersecurity researchers have disclosed two new attack techniques against infrastructure-as-code (IaC) and policy-as-code (PaC) tools like HashiCorp's Terraform and Open Policy Agent (OPA) that...

What do hijacked websites, fake job offers, and sneaky ransomware have in common? They’re proof that cybercriminals are finding smarter, sneakier ways to exploit both systems and people. This week...

According to Gartner, the broad range of pricing for government, risk, and compliance (GRC) tools requires enterprise risk management (ERM) leaders to be well-versed in distinct pricing tiers of...

Microsoft has finally confirmed that some Windows Server 2019 and 2022 systems were "unexpectedly" upgraded to Windows Server 2025 on devices if updates were managed using third-party patch...

⚠️ Imagine this: the very tools you trust to protect you online—your two-factor authentication, your car’s tech system, even your security software—turned into silent allies for hackers. Sounds...
High-profile entities in India have become the target of malicious campaigns orchestrated by the Pakistan-based Transparent Tribe threat actor and a previously unknown China-nexus cyber espionage...

There are a great many vulnerability management tools available. But which is best? Here are our top picks for a variety of use cases.