Security News

The U.S. Cybersecurity and Infrastructure Security Agency has given federal agencies three weeks to secure Adobe ColdFusion servers on their networks against two critical security flaws exploited in attacks, one of them as a zero-day. According to the binding operational directive issued by CISA in November 2021, Federal Civilian Executive Branch Agencies are required to patch their systems against all bugs added to the Known Exploited Vulnerabilities catalog.

Thousands of Citrix Netscaler ADC and Gateway servers exposed online are likely vulnerable against a critical remote code execution bug exploited by unauthenticated attackers in the wild as a zero-day. "We tag all IPs where we see a version hash in a Citrix instance. This is due fact that Citrix has removed version hash information in recent revisions," Shadowserver said.

Thousands of Citrix Netscaler ADC and Gateway servers exposed online are likely vulnerable against a critical remote code execution bug exploited by unauthenticated attackers in the wild as a zero-day. "We tag all IPs where we see a version hash in a Citrix instance. This is due fact that Citrix has removed version hash information in recent revisions," Shadowserver said.
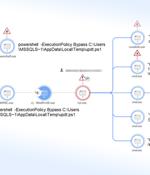
Mallox ransomware activities in 2023 have witnessed a 174% increase when compared to the previous year, new findings from Palo Alto Networks Unit 42 reveal. "Mallox ransomware, like many other ransomware threat actors, follows the double extortion trend: stealing data before encrypting an organization's files, and then threatening to publish the stolen data on a leak site as leverage to convince victims to pay the ransom fee," security researchers Lior Rochberger and Shimi Cohen said in a new report shared with The Hacker News.

Two more security flaws have been disclosed in AMI MegaRAC Baseboard Management Controller software that, if successfully exploited, could allow threat actors to remotely commandeer vulnerable servers and deploy malware. "These new vulnerabilities range in severity from High to Critical, including unauthenticated remote code execution and unauthorized device access with superuser permissions," Eclypsium researchers Vlad Babkin and Scott Scheferman said in a report shared with The Hacker News.

Two new critical severity vulnerabilities have been discovered in the MegaRAC Baseboard Management Controller software made by hardware and software company American Megatrends International. MegaRAC BMC provides admins with "Out-of-band" and "Lights-out" remote system management capabilities, enabling them to troubleshoot servers as if they were physically in front of the devices.

Turla has been targeting defense sector organizations in Ukraine and Eastern Europe with DeliveryCheck and Kazuar backdoors / infostealers and has been using compromised Microsoft Exchange servers to control them. Turla APT. Turla is a sophisticated and persistent APT group that has been active for over 10 years and is believed to be sponsored by the Russian state.

Earlier this month, security researchers discovered a new peer-to-peer malware with self-spreading capabilities that targets Redis instances running on Internet-exposed Windows and Linux systems. The Unit 42 researchers who spotted the Rust-based worm on July 11 also found that it hacks into Redis servers that have been left vulnerable to the maximum severity CVE-2022-0543 Lua sandbox escape vulnerability.
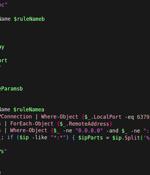
Cybersecurity researchers have uncovered a new cloud targeting, peer-to-peer worm called P2PInfect that targets vulnerable Redis instances for follow-on exploitation. "P2PInfect exploits Redis servers running on both Linux and Windows Operating Systems making it more scalable and potent than other worms," Palo Alto Networks Unit 42 researchers William Gamazo and Nathaniel Quist said.

Microsoft and the Ukraine CERT warn of new attacks by the Russian state-sponsored Turla hacking group, targeting the defense industry and Microsoft Exchange servers with a new 'DeliveryCheck' malware backdoor. The cyberspies have been associated with a wide array of attacks against Western interests over the years, including the Snake cyber-espionage malware botnet that was recently disrupted in an international law enforcement operation titled Operation MEDUSA. In a coordinated report and Twitter thread published today by CERT-UA and Microsoft, researchers outline a new attack where the Turla threat actors target the defense sector in Ukraine and Eastern Europe.