Security News

Cybersecurity researchers have disclosed details of a previously undocumented threat group called Unfading Sea Haze that's believed to have been active since 2018. The intrusion singled out...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

A critical security flaw has been disclosed in the llama_cpp_python Python package that could be exploited by threat actors to achieve arbitrary code execution. Tracked as CVE-2024-34359 (CVSS...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Security researchers have disclosed almost a dozen security flaws impacting the GE HealthCare Vivid Ultrasound product family that could be exploited by malicious actors to tamper with patient...
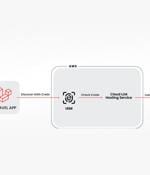
Cybersecurity researchers have discovered a novel attack that employs stolen cloud credentials to target cloud-hosted large language model (LLM) services with the goal of selling access to other...

Advertising presented to you on this service can be based on limited data, such as the website or app you are using, your non-precise location, your device type or which content you are interacting with. Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests.

Researchers have found two novel types of attacks that target the conditional branch predictor found in high-end Intel processors, which could be exploited to compromise billions of processors currently in use. The new paper, "Pathfinder: High-Resolution Control-Flow Attacks Exploiting the Conditional Branch Predictor," details two novel attacks that could compromise the billions of Intel processors in use.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Researchers have sinkholed a command and control server for a variant of the PlugX malware and observed in six months more than 2.5 million connections from unique IP addresses. Since September 2023, when Sekoia captured the unique IP address associated with the particular C2, it has logged over 2,495,297 unique IPs from 170 countries interacting with its sinkhole.