Security News

A new wave of a mobile surveillance campaign has been observed targeting the Uyghur community as part of a long-standing spyware operation active since at least 2015, cybersecurity researchers disclosed Thursday. It's worth noting that a part of the campaign was recently disclosed by researchers from the MalwareHunterTeam and Cyble, in which a book written by the exiled Uyghur leader Dolkun Isa was used as a lure to deliver the malware.
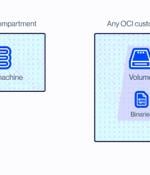
Researchers have disclosed a new severe Oracle Cloud Infrastructure vulnerability that could be exploited by users to access the virtual disks of other Oracle customers. "Each virtual disk in Oracle's cloud has a unique identifier called OCID," Shir Tamari, head of research at Wiz, said in a series of tweets.

Cybersecurity researchers have exposed new connections between a widely used pay-per-install malware service known as PrivateLoader and another PPI service dubbed ruzki. "The threat actor ruzki advertises their PPI service on underground Russian-speaking forums and their Telegram channels under the name ruzki or zhigalsz since at least May 2021," SEKOIA said.

Gamers looking for cheats on YouTube are being targeted with links to malicious password-protected archive files designed to install the RedLine Stealer malware and crypto miners on compromised machines. "The videos advertise cheats and cracks and provide instructions on hacking popular games and software," Kaspersky security researcher Oleg Kupreev said in a new report published today.

Palo Alto Networks Unit 42 has detailed the inner workings of a malware called OriginLogger, which has been touted as a successor to the widely used information stealer and remote access trojan known as Agent Tesla. A.NET based keylogger and remote access, Agent Tesla has had a long-standing presence in the threat landscape, allowing malicious actors to gain remote access to targeted systems and beacon sensitive information to an actor-controlled domain.

PQShield published a white paper that lays out the quantum threat to secure end-to-end messaging and explains how post-quantum cryptography can be added to the Signal secure messaging protocol to protect it from quantum attacks. The company is offering to license its end-to-end encrypted messaging IP to the Signal Foundation pro bono - if/when they plan to upgrade their system - to support the non-profit behind the free encrypted messaging app, Signal, in its mission to make secure communication accessible to everyone.

A previously undocumented strain of Android spyware with extensive information gathering capabilities has been found disguised as a book likely designed to target the Uyghur community in China. The malware comes under the guise of a book titled "The China Freedom Trap," a biography written by the exiled Uyghur leader Dolkun Isa.

The operators of the emerging cross-platform BianLian ransomware have increased their command-and-control infrastructure this month, a development that alludes to an increase in the group's operational tempo. "BianLian has also targeted SonicWall VPN devices for exploitation, another common target for ransomware groups," [redacted] researchers Ben Armstrong, Lauren Pearce, Brad Pittack, and Danny Quist said.
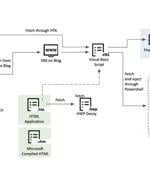
The North Korean nation-state group Kimusky has been linked to a new set of malicious activities directed against political and diplomatic entities located in its southern counterpart in early 2022. Included among the potential victims are South Korean university professors, think tank researchers, and government officials.
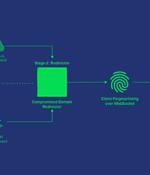
The threat actors behind a large-scale adversary-in-the-middle phishing campaign targeting enterprise users of Microsoft email services have also set their sights on Google Workspace users. The AitM phishing attacks are said to have commenced in mid-July 2022, following a similar modus operandi as that of a social engineering campaign designed to siphon users' Microsoft credentials and even bypass multi-factor authentication.