Security News
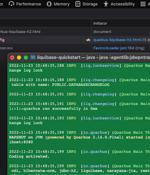
A critical security vulnerability has been disclosed in the Quarkus Java framework that could be potentially exploited to achieve remote code execution on affected systems. "The vulnerability is found in the Dev UI Config Editor, which is vulnerable to drive-by localhost attacks that could lead to remote-code execution," Contrast Security researcher Joseph Beeton, who reported the bug, said in a write-up.
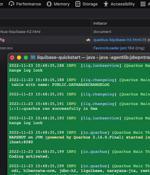
A critical security vulnerability has been disclosed in the Quarkus Java framework that could be potentially exploited to achieve remote code execution on affected systems. "The vulnerability is found in the Dev UI Config Editor, which is vulnerable to drive-by localhost attacks that could lead to remote-code execution," Contrast Security researcher Joseph Beeton, who reported the bug, said in a write-up.

An ongoing analysis into an up-and-coming cryptocurrency mining botnet known as KmsdBot has led to it being accidentally taken down. The botnet strikes both Windows and Linux devices spanning a wide range of microarchitectures with the primary goal of deploying mining software and corralling the compromised hosts into a DDoS bot.

While analyzing its capabilities, Akamai researchers have accidentally taken down a cryptomining botnet that was also used for distributed denial-of-service attacks. As revealed in a report published earlier this month, the KmsdBot malware behind this botnet was discovered by members of the Akamai Security Intelligence Response Team after it infected one of their honeypots.
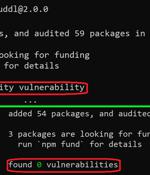
New findings from cybersecurity firm JFrog show that malware targeting the npm ecosystem can evade security checks by taking advantage of an "Unexpected behavior" in the npm command line interface tool. Npm CLI's install and audit commands have built-in capabilities to check a package and all of its dependencies for known vulnerabilities, effectively acting as a warning mechanism for developers by highlighting the flaws.
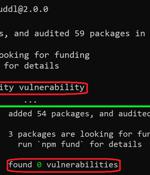
New findings from cybersecurity firm JFrog show that malware targeting the npm ecosystem can evade security checks by taking advantage of an "Unexpected behavior" in the npm command line interface tool. Npm CLI's install and audit commands have built-in capabilities to check a package and all of its dependencies for known vulnerabilities, effectively acting as a warning mechanism for developers by highlighting the flaws.

Amazon Web Services has resolved a cross-tenant vulnerability in its platform that could be weaponized by an attacker to gain unauthorized access to resources. "This attack abuses the AppSync service to assume roles in other AWS accounts, which allows an attacker to pivot into a victim organization and access resources in those accounts," Datadog researcher Nick Frichette said in a report published last week.

Amazon Web Services has resolved a cross-tenant vulnerability in its platform that could be weaponized by an attacker to gain unauthorized access to resources."This attack abuses the AppSync service to assume roles in other AWS accounts, which allows an attacker to pivot into a victim organization and access resources in those accounts," Datadog researcher Nick Frichette said in a report published last week.

A nascent Go-based malware known as Aurora Stealer is being increasingly deployed as part of campaigns designed to steal sensitive information from compromised hosts. First advertised on Russian cybercrime forums in April 2022, Aurora was offered as a commodity malware for other threat actors, describing it as a "Multi-purpose botnet with stealing, downloading and remote access capabilities."

In brief A security researcher whose Google Pixel battery died while sending a text is probably thankful for the interruption - powering it back up led to a discovery that netted him a $70,000 bounty from Google for a lock screen bypass bug. Hungarian security researcher David Schütz said in a blog post that he made the discovery when powering up his Pixel 6 and forgetting his SIM's PIN code, requiring him to dig out the Personal Unlocking Key, or PUK, that would allow him to reset the PIN. After a reboot, his phone repeatedly hung on a "Pixel is starting" screen.