Security News

Cybersecurity researchers have flagged a new malicious campaign related to the North Korean state-sponsored threat actor known as Kimsuky that exploits a now-patched vulnerability impacting...

Remote Desktop Protocol (RDP) is an amazing technology developed by Microsoft that lets you access and control another computer over a network. It’s like having your office computer with you...

Cloud-based RDP Remote Desktop Protocol solutions offer a centralized dashboard to manage user access, security policies, and monitor usage from one location. Learn more from TruGrid about how...

The North Korean hacking group known as Kimsuky was observed in recent attacks using a custom-built RDP Wrapper and proxy tools to directly access infected machines. [...]

Remote work is now an essential part of many businesses, requiring organizations to rethink how they provide secure and efficient access to corporate resources. Learn from TruGrid about the...

The Russian hacking group tracked as APT29 (aka "Midnight Blizzard") is using a network of 193 remote desktop protocol proxy servers to perform man-in-the-middle (MiTM) attacks to steal data and...

The Russia-linked APT29 threat actor has been observed repurposing a legitimate red teaming attack methodology as part of cyber attacks leveraging malicious Remote Desktop Protocol (RDP)...

Midnight Blizzard – a cyber espionage group that has been linked to the Russian Foreign Intelligence Service (SVR) – is targeting government, academia, defense, and NGO workers with phishing...
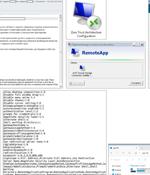
The Computer Emergency Response Team of Ukraine (CERT-UA) has detailed a new malicious email campaign targeting government agencies, enterprises, and military entities. "The messages exploit the...

Sandu Diaconu, the operator of the E-Root marketplace, has been extradited to the U.S. to face a maximum imprisonment penalty of 20 years for selling access to compromised computers. Last month, Diaconu consented to be extradited to the United States for wire fraud, money laundering, computer fraud, and access device fraud.