Security News

Microsoft says the Scattered Spider cybercrime gang has added Qilin ransomware to its arsenal and is now using it in attacks. "In the second quarter of 2024, financially motivated threat actor Octo Tempest, our most closely tracked ransomware threat actor, added RansomHub and Qilin to its ransomware payloads in campaigns," Microsoft said Monday.

The SEXi ransomware operation, known for targeting VMware ESXi servers, has rebranded under the name APT INC and has targeted numerous organizations in recent attacks. The ransomware operation was given the name SEXi based on the SEXi.txt ransom note name and the.

Cybersecurity researchers have shed light on a new version of a ransomware strain called HardBit that comes packaged with new obfuscation techniques to deter analysis efforts. "Unlike previous versions, HardBit Ransomware group enhanced the version 4.0 with passphrase protection," Cybereason researchers Kotaro Ogino and Koshi Oyama said in an analysis.

Pharmacy giant Rite Aid confirmed a data breach after suffering a cyberattack in June, which was claimed by the RansomHub ransomware operation. The company told BleepingComputer on Friday that it's currently investigating a cyberattack detected in June and working on sending data breach notifications to customers affected by the resulting data breach.

The American Radio Relay League (ARRL) finally confirmed that some of its employees' data was stolen in a May ransomware attack initially described as a "serious incident." [...]

Dallas County is notifying over 200,000 people that the Play ransomware attack, which occurred in October 2023, exposed their personal data to cybercriminals. Dallas County is the second largest county in Texas, with over 2.6 million residents.

Cisco Talos analyzed the top 14 ransomware groups between 2023 and 2024 to expose their attack chain and highlight interesting Tactics,Techniques and Protocols. The security company also exposed the most leveraged vulnerabilities being triggered by ransomware actors.

Fujitsu Japan says an unspecified "Advanced" malware strain was to blame for a March data theft, insisting the strain was "Not ransomware", yet it hasn't revealed how many individuals are affected. Despite initially downplaying the likelihood of data theft, Fujitsu confirmed on Tuesday that affected individuals had been directly notified.
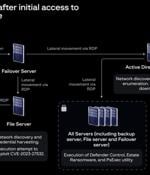
A now-patched security flaw in Veeam Backup & Replication software is being exploited by a nascent ransomware operation known as EstateRansomware. "Before the ransomware attack, there were VPN brute-force attempts noted in April 2024 using a dormant account identified as 'Acc1.' Several days later, a successful VPN login using 'Acc1' was traced back to the remote IP address 149.28.106[.]252.".

As ransomware crews increasingly shift beyond just encrypting victims' files and demanding a payment to unlock them, instead swiping sensitive info straight away, some of the more mature crime organizations are developing custom malware for their data theft. "Over the past year, we have witnessed major shifts in the ransomware space with the emergence of multiple new ransomware groups, each exhibiting unique goals, operational structures and victimology," the report's authors note.