Security News

An unknown threat actor is targeting German users interested in the Ukraine crisis, infecting them with a custom PowerShell RAT and stealing their data. These sites offer malicious documents that install a custom RAT that supports remote command execution and file operations.

You can find the date of the user's most recent password change by examining the PwdLastSet attribute, shown in Figure 1. Only one user's password change date is being shown, but there are any number of ways to tell the Get-ADUser cmdlet to display data for multiple user accounts.

The Emotet botnet is now using Windows shortcut files containing PowerShell commands to infect victims computers, moving away from Microsoft Office macros that are now disabled by default. LNK files is not new, as the Emotet gang previously used them in a combination with Visual Basic Script code to build a command that downloads the payload. However, this is the first time that they utilized Windows shortcuts to directly execute PowerShell commands.

The Iranian advanced persistent threat Charming Kitten is sharpening its claws with a new set of tools, including a novel PowerShell backdoor and related stealth tactics, that show the group evolving yet again. Researchers at cybersecurity firm Cybereason discovered the tools, which include a backdoor they dubbed "PowerLess Backdoor," as well as an evasive maneuver to run the backdoor in a.NET context rather than as one that triggers a PowerShell process, the Cybereason Nocturnus Team wrote in a report published Tuesday.

An Iranian state-backed hacking group tracked as APT35 is now deploying a new backdoor called PowerLess and developed using PowerShell. "The toolset analyzed includes extremely modular, multi-staged malware that decrypts and deploys additional payloads in several stages for the sake of both stealth and efficacy. At the time of writing this report, some of the IOCs remained active delivering new payloads," the Cybereason researchers said.
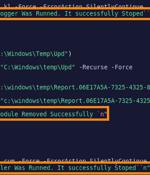
An advanced persistent threat group with links to Iran has updated its malware toolset to include a novel PowerShell-based implant called PowerLess Backdoor, according to new research published by Cybereason. The Boston-headquartered cybersecurity company attributed the malware to a hacking group known as Charming Kitten, while also calling out the backdoor's evasive PowerShell execution.
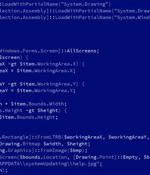
An Iranian state-sponsored actor has been observed scanning and attempting to abuse the Log4Shell flaw in publicly-exposed Java applications to deploy a hitherto undocumented PowerShell-based modular backdoor dubbed "CharmPower" for follow-on post-exploitation. Log4Shell aka CVE-2021-44228 concerns a critical security vulnerability in the popular Log4j logging library that, if successfully exploited, could lead to remote execution of arbitrary code on compromised systems.

Hackers believed to be part of the Iranian APT35 state-backed group has been observed leveraging Log4Shell attacks to drop a new PowerShell backdoor. As part of their research, the analysts also spotted something new in the form of a PowerShell modular backdoor named 'CharmPower.

If you've ever had a need to SSH into a Windows machine, Jack Wallen shows you how to make that possible with the help of PowerShell. I'm going to walk you through the process of installing the OpenSSH Server on Windows 10, configuring it to start at boot, and then show you how to log in from a Linux machine.

Microsoft has released PowerShell 7.2 with automatic updates through the Microsoft Update service on Windows 10 and Windows Server devices. "We have integration with Microsoft Update to automatically keep your installation of 7.2 updated whenever we have a servicing release which only includes critical bug fixes or security updates," said Steve Lee, Principal Software Engineer Manager for PowerShell.