Security News

Arcserve has fixed critical security vulnerabilities in its Unified Data Protection solution, PoCs for which have been published by Tenable researchers on Monday. Arcserve UDP is a popular enterprise data protection, backup and disaster recovery solution that improves organizations' resilience to ransomware attacks.

A proof-of-concept exploit for a high-severity flaw in Splunk Enterprise that can lead to remote code execution has been made public. Splunk Enterprise is a solution that ingests a variety of data generated by an organization's business infrastructure and applications.

Cybersecurity researchers have demonstrated a new technique that exploits a critical security flaw in Apache ActiveMQ to achieve arbitrary code execution in memory. Tracked as CVE-2023-46604 (CVSS...

F5 Networks has released hotfixes for three vulnerabilities affecting its BIG-IP multi-purpose networking devices/modules, including a critical authentication bypass vulnerability that could lead to unauthenticated remote code execution. "This vulnerability may allow an unauthenticated attacker with network access to the BIG-IP system through the management port and/or self IP addresses to execute arbitrary system commands," F5 confirmed.
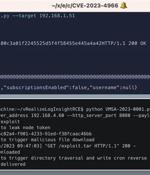
Virtualization services provider VMware has alerted customers to the existence of a proof-of-concept (PoC) exploit for a recently patched security flaw in Aria Operations for Logs. Tracked as...

Citrix has urged admins to "Immediately" apply a fix for CVE-2023-4966, a critical information disclosure bug that affects NetScaler ADC and NetScaler Gateway, admitting it has been exploited. Plus, there's a proof-of-concept exploit, dubbed Citrix Bleed, now on GitHub.

An unknown threat actor has released a fake proof of concept exploit for CVE-2023-4047, a recently fixed remote code execution vulnerability in WinRAR, to spread the VenomRAT malware. The fake WinRAR PoC. On August 17, 2023, Trend Micro's Zero Day Initiative reported the RCE vulnerability that allowed threat actors to execute arbitrary code on an affected WinRAR installation.

What does optimal software security analysis look like?In this Help Net Security interview, Kevin Valk, co-CEO at Codean, discusses the consequences of relying solely on automated tools for software security. Apple offers security researchers specialized iPhones to tinker withApple is inviting security researchers to apply for its Security Research Device Program again, to discover vulnerabilities and earn bug bounties.
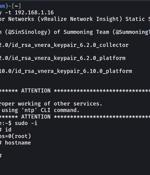
Proof-of-concept exploit code has been made available for a recently disclosed and patched critical flaw impacting VMware Aria Operations for Networks. "A malicious actor with network access to Aria Operations for Networks could bypass SSH authentication to gain access to the Aria Operations for Networks CLI," VMware said earlier this week.

Hackers are using a critical exploit chain to target Juniper EX switches and SRX firewalls via their Internet-exposed J-Web configuration interface. One week after Juniper disclosed and released security updates to patch the four flaws that can be chained to achieve remote code execution, watchTowr Labs security researchers released a proof-of-concept exploit targeting the SRX firewall bugs.