Security News

ChatGPT's Deep Research, which allows you to conduct multi-step research for complex tasks, is finally getting an option to save the report as a PDF. [...]

Microsoft is warning of several phishing campaigns that are leveraging tax-related themes to deploy malware and steal credentials. "These campaigns notably use redirection methods such as URL...

Cybersecurity researchers have uncovered a widespread phishing campaign that uses fake CAPTCHA images shared via PDF documents hosted on Webflow's content delivery network (CDN) to deliver the...

A widespread phishing campaign has been observed leveraging bogus PDF documents hosted on the Webflow content delivery network (CDN) with an aim to steal credit card information and commit...

Google is adding the Text Fragment feature to its PDF reader to make it easier to share specific parts of long PDFs. [...]

Microsoft is improving Copilot integration in the Edge browser with AI-powered smart keywords. This will allow the AI to generate important keywords from the PDF and then help you analyze each topic. [...]

A critical security flaw has been disclosed in the llama_cpp_python Python package that could be exploited by threat actors to achieve arbitrary code execution. Tracked as CVE-2024-34359 (CVSS...
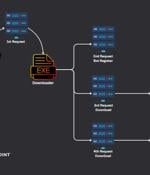
Multiple threat actors are weaponizing a design flaw in Foxit PDF Reader to deliver a variety of malware such as Agent Tesla, AsyncRAT, DCRat, NanoCore RAT, NjRAT, Pony, Remcos RAT, and XWorm....

Threat actors are taking advantage of the flawed design of Foxit PDF Reader's alerts to deliver malware via booby-trapped PDF documents, Check Point researchers have warned. The researchers have analyzed several campaigns using malicious PDF files that are targeting Foxit Reader users.

The tech world has a problem: Security fragmentation. There's no standard set of rules or even language for mitigating cyber risk used to address the growing threats of hackers, ransomware and stolen data, and the threat to data only continues to grow.