Security News

Google on Thursday rolled out an emergency update for its Chrome web browser, including fixes for two zero-day vulnerabilities that it says are being actively exploited in the wild. The internet giant's Threat Analysis Group has been credited with discovering and reporting the two flaws on September 15, 2021, and October 26, 2021, respectively.

These couldn't wait for Patch Tuesday: Adobe issues bonus fixes for 92 security holes in 14 products
A mere two weeks after its most recent set of security patches, Adobe has issued another 14 security bulletins covering 92 CVE-listed bugs. Adobe's repairs apparently represent planned maintenance rather than an out-of-band release, even though October's Patch Tuesday - the second Tuesday of the month - has come and gone.

Discourse - the ultra-popular, widely deployed open-source community forum and mailing list management platform - has a critical remote code-execution bug that was fixed in an urgent update on Friday. Discourse is widely used and wildly popular, being known for topping competing forum software platforms in terms of usability.

A critical Discourse remote code execution vulnerability tracked as CVE-2021-41163 was fixed via an urgent update by the developer on Friday. Discourse is an open-source forum, long-form chat, and mailing list management platform widely deployed on the web, offering excellent usability and integration potential while focusing heavily on social features.
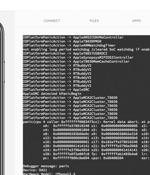
CVE-2021-30663 - Processing maliciously crafted web content may lead to arbitrary code execution. CVE-2021-30665 - Processing maliciously crafted web content may lead to arbitrary code execution.

Microsoft has asked system administrators to patch PowerShell 7 against two vulnerabilities allowing attackers to bypass Windows Defender Application Control enforcements and gain access to plain text credentials. PowerShell is a cross-platform solution that provides a command-line shell, a framework, and a scripting language focused on automation for processing PowerShell cmdlets.

Microsoft on Tuesday rolled out security patches to contain a total of 71 vulnerabilities in Microsoft Windows and other software, including a fix for an actively exploited privilege escalation vulnerability that could be exploited in conjunction with remote code execution bugs to take control over vulnerable systems. At the top of the list is CVE-2021-40449, a use-after-free vulnerability in the Win32k kernel driver discovered by Kaspersky as being exploited in the wild in late August and early September 2021 as part of a widespread espionage campaign targeting IT companies, defense contractors, and diplomatic entities.
![S3 Ep54: Another 0-day, double Apache patch, and Fight The Phish [Podcast]](/static/build/img/news/s3-ep54-another-0-day-double-apache-patch-and-fight-the-phish-podcast-small.jpg)

Today is Microsoft's October 2021 Patch Tuesday, and it delivers fixes for four zero-day vulnerabilities, one of which is being exploited in a far-reaching espionage campaign that delivers the new MysterySnail RAT malware to Windows servers. Bharat Jogi, Qualsys senior manager of vulnerability and threat research, told Threatpost on Tuesday that if left unpatched, "MysterySnail has the potential to collect and exfiltrate system information from compromised hosts, in addition to other malicious users having the ability to gain complete control of the affected system and launch further attacks."

Microsoft's October Patch Tuesday has arrived with fixes for 71 new CVEs, two patch revisions to address bugs from previous months that just won't die, and three CVEs tied to OpenSSL flaws. Microsoft says one of the bugs, a Win32K privilege elevation issue is currently being exploited.