Security News

Fujitsu Japan says an unspecified "Advanced" malware strain was to blame for a March data theft, insisting the strain was "Not ransomware", yet it hasn't revealed how many individuals are affected. Despite initially downplaying the likelihood of data theft, Fujitsu confirmed on Tuesday that affected individuals had been directly notified.
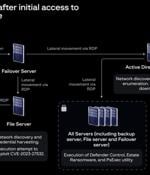
A now-patched security flaw in Veeam Backup & Replication software is being exploited by a nascent ransomware operation known as EstateRansomware. "Before the ransomware attack, there were VPN brute-force attempts noted in April 2024 using a dormant account identified as 'Acc1.' Several days later, a successful VPN login using 'Acc1' was traced back to the remote IP address 149.28.106[.]252.".

CVE-2024-38112, a spoofing vulnerability in Windows MSHTML Platform for which Microsoft has released a fix on Tuesday, has likely been exploited by attackers in the wild for over a year, Check Point researcher Haifei Li has revealed. "Check Point Research recently discovered that threat actors have been using novel tricks to lure Windows users for remote code execution. Specifically, the attackers used special Windows Internet Shortcut files, which, when clicked, would call the retired Internet Explorer to visit the attacker-controlled URL," he explained.

As shown, mission-critical firmware, security firmware, and handler mode firmware are protected by the pmode barrier and run in privileged mode or hmode. As shown in the figure, umode firmware is divided into isolated partitions.

Microsoft has released patches to address a total of 143 security flaws as part of its monthly security updates, two of which have come under active exploitation in the wild. Five out of the 143 flaws are rated Critical, 136 are rated Important, and four are rated Moderate in severity.

What questions to ask:# Does the ITDR also cover non-human identities, such as Active Directory service accounts? Can the ITDR analyze the full authentication trail of users, across on-prem resources, cloud workloads and SaaS apps? Would the ITDR detect malicious access over command line access tools such as PsExec or PowerShell? Why is it important?#. What questions to ask:# Does the ITDR solution integrate directly with on-prem and cloud Identity Providers to analyze authentications as they happen? Does the ITDR query the IDP to detect changes in account configuration? Why is it important?#.
Google has removed a potential obstacle for high-risk users who want to enroll in the company's Advanced Protection Program: they can now do it just by setting a passkey. Until now, new users were required to have two physical security keys to enroll in the first place.

A large-scale fraud campaign with over 700 domain names is likely targeting Russian-speaking users looking to purchase tickets for the Summer Olympics in Paris. Researchers analyzing the campaign are calling it Ticket Heist and found that some of the domains were created in 2022 and the threat actor kept registering an average of 20 new ones every month.

A large-scale fraud campaign with over 700 domain names is likely targeting Russian-speaking users looking to purchase tickets for the Summer Olympics in Paris. [...]
Google on Wednesday announced that it's making available passkeys for high-risk users to enroll in its Advanced Protection Program. Based on the FIDO Authentication standard, the technology is designed to secure online accounts against potential takeover attacks by ditching passwords in favor of biometrics or a PIN. Passkeys can simultaneously act as a first- and second-factor, entirely obviating the need for a password.