Security News

Advertising presented to you on this service can be based on limited data, such as the website or app you are using, your non-precise location, your device type or which content you are interacting with. Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests.
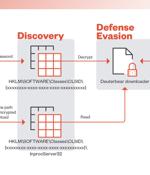
Technology, research, and government sectors in the Asia-Pacific region have been targeted by a threat actor called BlackTech as part of a recent cyber attack wave. The intrusions pave the way for...

More organizations hit by ransomware gangs are starting to realize that it doesn't pay to pay up: "In Q1 2024, the proportion of victims that chose to pay touched a new record low of 28%," ransomware incident response firm Coveware has found. "LockBit was found to still be holding the stolen data of victims that had paid a ransom, and we have also seen prior Hive victims that had paid the extortion, have their data posted on the Hunters International leak site," the company said, noting that "Future victims of data exfiltration extortion are getting more evidence daily that payments to suppress leaks have little efficacy in the short and long term."

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.
Attackers are increasingly making use of “networkless” attack techniques targeting cloud apps and identities. Here’s how attackers can (and are) compromising organizations – without ever needing...

Threat actors behind the Akira ransomware group have extorted approximately $42 million in illicit proceeds after breaching the networks of more than 250 victims as of January 1, 2024. "Since...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

The CryptoChameleon phishing kit is being leveraged by vishing attackers looking to trick LastPass users into sharing their master password. "Initially, we learned of a new parked domain and immediately marked the website for monitoring should it go live and start serving a phishing site intended to imitate our login page or something similar. Once we identified that this site went active and was being used in a phishing campaign against our customers, we worked with our vendor to take down the site," LastPass intelligence analyst Mike Kosak explained.

Government entities in the Middle East have been targeted as part of a previously undocumented campaign to deliver a new backdoor dubbed CR4T. Russian cybersecurity company Kaspersky said it...

Protobom is an open-source software supply chain tool that enables all organizations, including system administrators and software development communities, to read and generate Software Bill of Materials, file data, and translate this data across standard industry SBOM formats. The key to strengthening software security and software supply chain risk management is an SBOM, which is a nested, formatted inventory that lists the software's components, including the supply chain relationships of various open-source and commercial components used in building software.