Security News
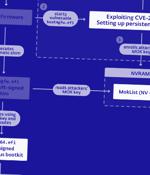
The U.S. National Security Agency on Thursday released guidance to help organizations detect and prevent infections of a Unified Extensible Firmware Interface bootkit called BlackLotus. A UEFI bootkit capable of bypassing Windows Secure Boot protections, samples of the malware have since emerged in the wild.

The U.S. National Security Agency released today guidance on how to defend against BlackLotus UEFI bootkit malware attacks. In May, Microsoft released security updates to address a Secure Boot zero-day vulnerability that was used to bypass patches released for CVE-2022-21894, the Secure Boot bug initially abused in BlackLotus attacks last year.

State-sponsored North Korean hacker group Kimsuky has been impersonating journalists and academics for spear-phishing campaigns to collect intelligence from think tanks, research centers, academic institutions, and various media organizations. Kimsuky hackers meticulously plan and execute their spear-phishing attacks by using email addresses that closely resemble those of real individuals and by crafting convincing, realistic content for the communication with the target.

Russian intelligence has accused American snoops and Apple of working together to backdoor iPhones to spy on "Thousands" of diplomats worldwide. A Kaspersky spokesperson told The Register it's aware of the FSB claims, but can't say if the two things - Uncle Sam backdooring iPhones, and the spyware found on several Kaspersky devices - are linked.

Access control has become a main concern when it comes to developing secure web applications, and the NSA has a lot to say about it. In this article, we will focus and elaborate on the best practices offered by the NSA for building secure access management, and how they can be implemented at the application level.

The U.S. National Security Agency has issued guidance to help remote workers secure their home networks and defend their devices from attacks. "At a minimum, you should schedule weekly reboots of your routing device, smartphones, and computers. Regular reboots help to remove implants and ensure security," the NSA said.
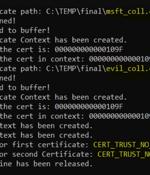
Proof-of-concept (Poc) code has been released for a now-patched high-severity security flaw in the Windows CryptoAPI that the U.S. National Security Agency (NSA) and the U.K. National Cyber...

Most Windows-powered datacenter systems and applications remain vulnerable to a spoofing bug in CryptoAPI that was disclosed by the NSA and the UK National Cyber Security Center and patched by Microsoft last year, according to Akamai's researchers. The bug isn't a remote code execution flaw; it's a vulnerability that allows someone to pretend to be another to an application or operating system, in the context of identity and certificate cryptography checks on Windows.

NSA director General Paul Nakasone told the Privacy and Civil Liberties Oversight Board yesterday that the loss of Section 702 of the Foreign Intelligence Surveillance Act would mean American spies would "Lose critical insights into the most significant threats to our nation" if allowed to lapse on December 31. In his speech, Nakasone said Section 702 is "Irreplaceable," and he provided several stories of the FBI and NSA cooperating using the law to stop terrorist plots and online attacks to justify his claim.

The National Security Agency, the Cybersecurity and Infrastructure Security Agency, and the Office of the Director of National Intelligence, have published a joint report that highlights the most likely risks and potential threats in 5G network slicing implementations. The 5G network slicing report builds upon Potential Threat Vectors to 5G Infrastructure, a paper published last year by the Enduring Security Framework cross-sector working group focused on addressing risks and threats to the security and stability of U.S. national security systems.