Security News

Dalke, 31, admitted that he transmitted excerpts from three classified documents, and sent four in their entirety, to an FBI online covert employee, all of which contained national defense information determined [PDF] to be classified top secret. A former US Army soldier, Dalke was employed at the NSA as an information security systems designer for less than a month, and resigned after the NSA denied his request for extended leave to take care of a sick family member.

A former employee of the U.S. National Security Agency (NSA) has pleaded guilty to charges accusing him of attempting to transmit classified defense information to Russia. Jareh Sebastian Dalke,...

Cyber entities continue to show a persistent interest in targeting critical infrastructure by taking advantage of vulnerable OT assets. To counter this threat, NSA has released a repository for OT...

In an email interview with TechRepublic, Jake Williams, faculty member at IANS Research and former NSA offensive hacker, said, "The publication highlights the challenges with comparing the features provided by vendors. CISA seems to be putting vendors on notice that they want vendors to be clear about what standards they do and don't support in their products, especially when a vendor only supports portions of a given standard." According to CISA and the NSA, the definitions and policies of the different variations of MFAs are unclear and confusing.

A bounty of $12,288 has been announced for the first person to crack the NIST elliptic curves seeds and discover the original phrases that were hashed to generate them. In Elliptic Curve Cryptography, seeds are values or sets of values used as the initial input for an encryption algorithm or process to produce cryptographic keys.

The National Security Agency and the Cybersecurity and Infrastructure Security Agency revealed today the top ten most common cybersecurity misconfigurations discovered by their red and blue teams in the networks of large organizations. "These teams have assessed the security posture of many networks across the Department of Defense, Federal Civilian Executive Branch, state, local, tribal, and territorial governments, and the private sector," the NSA said.

The AI security center's establishment follows an NSA study that identified securing AI models from theft and sabotage as a major national security challenge, especially as generative AI technologies emerge with immense transformative potential for both good and evil. Nakasone said it would become "NSA's focal point for leveraging foreign intelligence insights, contributing to the development of best practices guidelines, principles, evaluation, methodology and risk frameworks" for both AI security and the goal of promoting the secure development and adoption of AI within "Our national security systems and our defense industrial base."

In collaboration with CISA, the NSA, and the FBI, Five Eyes cybersecurity authorities have issued today a list of the 12 most exploited vulnerabilities throughout 2022."In 2022, malicious cyber actors exploited older software vulnerabilities more frequently than recently disclosed vulnerabilities and targeted unpatched, internet-facing systems," the joint advisory reads.

U.S. cybersecurity and intelligence agencies have released a set of recommendations to address security concerns with 5G standalone network slicing and harden them against possible threats. "The threat landscape in 5G is dynamic; due to this, advanced monitoring, auditing, and other analytical capabilities are required to meet certain levels of network slicing service level requirements over time," the U.S. Cybersecurity and Infrastructure Security Agency and the National Security Agency said.
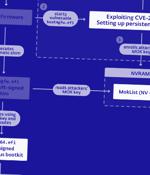
The U.S. National Security Agency on Thursday released guidance to help organizations detect and prevent infections of a Unified Extensible Firmware Interface bootkit called BlackLotus. A UEFI bootkit capable of bypassing Windows Secure Boot protections, samples of the malware have since emerged in the wild.