Security News

A bounty of $12,288 has been announced for the first person to crack the NIST elliptic curves seeds and discover the original phrases that were hashed to generate them. In Elliptic Curve Cryptography, seeds are values or sets of values used as the initial input for an encryption algorithm or process to produce cryptographic keys.

The National Security Agency and the Cybersecurity and Infrastructure Security Agency revealed today the top ten most common cybersecurity misconfigurations discovered by their red and blue teams in the networks of large organizations. "These teams have assessed the security posture of many networks across the Department of Defense, Federal Civilian Executive Branch, state, local, tribal, and territorial governments, and the private sector," the NSA said.

The AI security center's establishment follows an NSA study that identified securing AI models from theft and sabotage as a major national security challenge, especially as generative AI technologies emerge with immense transformative potential for both good and evil. Nakasone said it would become "NSA's focal point for leveraging foreign intelligence insights, contributing to the development of best practices guidelines, principles, evaluation, methodology and risk frameworks" for both AI security and the goal of promoting the secure development and adoption of AI within "Our national security systems and our defense industrial base."

In collaboration with CISA, the NSA, and the FBI, Five Eyes cybersecurity authorities have issued today a list of the 12 most exploited vulnerabilities throughout 2022."In 2022, malicious cyber actors exploited older software vulnerabilities more frequently than recently disclosed vulnerabilities and targeted unpatched, internet-facing systems," the joint advisory reads.

U.S. cybersecurity and intelligence agencies have released a set of recommendations to address security concerns with 5G standalone network slicing and harden them against possible threats. "The threat landscape in 5G is dynamic; due to this, advanced monitoring, auditing, and other analytical capabilities are required to meet certain levels of network slicing service level requirements over time," the U.S. Cybersecurity and Infrastructure Security Agency and the National Security Agency said.
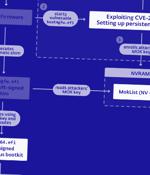
The U.S. National Security Agency on Thursday released guidance to help organizations detect and prevent infections of a Unified Extensible Firmware Interface bootkit called BlackLotus. A UEFI bootkit capable of bypassing Windows Secure Boot protections, samples of the malware have since emerged in the wild.

The U.S. National Security Agency released today guidance on how to defend against BlackLotus UEFI bootkit malware attacks. In May, Microsoft released security updates to address a Secure Boot zero-day vulnerability that was used to bypass patches released for CVE-2022-21894, the Secure Boot bug initially abused in BlackLotus attacks last year.

State-sponsored North Korean hacker group Kimsuky has been impersonating journalists and academics for spear-phishing campaigns to collect intelligence from think tanks, research centers, academic institutions, and various media organizations. Kimsuky hackers meticulously plan and execute their spear-phishing attacks by using email addresses that closely resemble those of real individuals and by crafting convincing, realistic content for the communication with the target.

Russian intelligence has accused American snoops and Apple of working together to backdoor iPhones to spy on "Thousands" of diplomats worldwide. A Kaspersky spokesperson told The Register it's aware of the FSB claims, but can't say if the two things - Uncle Sam backdooring iPhones, and the spyware found on several Kaspersky devices - are linked.

Access control has become a main concern when it comes to developing secure web applications, and the NSA has a lot to say about it. In this article, we will focus and elaborate on the best practices offered by the NSA for building secure access management, and how they can be implemented at the application level.