Security News

A malicious crypto mining campaign codenamed 'REF4578,' has been discovered deploying a malicious payload named GhostEngine that uses vulnerable drivers to turn off security products and deploy an XMRig miner. Researchers at Elastic Security Labs and Antiy have underlined the unusual sophistication of these crypto-mining attacks in separate reports and shared detection rules to help defenders identify and stop them.

Cybersecurity researchers are warning that threat actors are actively exploiting a "disputed" and unpatched vulnerability in an open-source artificial intelligence (AI) platform called Anyscale...

Threat actors are targeting misconfigured and vulnerable servers running Apache Hadoop YARN, Docker, Atlassian Confluence, and Redis services as part of an emerging malware campaign designed to...

A novel malware campaign has been observed targeting Redis servers for initial access with the ultimate goal of mining cryptocurrency on compromised Linux hosts. "This particular campaign involves...

Cybersecurity researchers have detailed an updated version of the malware HeadCrab that's known to target Redis database servers across the world since early September 2021. The development, which...

A new Mirai-based botnet called NoaBot is being used by threat actors as part of a crypto mining campaign since the beginning of 2023. “The capabilities of the new botnet, NoaBot, include a...
Poorly secured Linux SSH servers are being targeted by bad actors to install port scanners and dictionary attack tools with the goal of targeting other vulnerable servers and co-opting them into a...
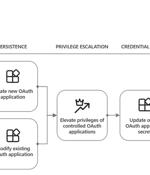
Microsoft has warned that adversaries are using OAuth applications as an automation tool to deploy virtual machines (VMs) for cryptocurrency mining and launch phishing attacks. "Threat actors...
Cybersecurity researchers have developed what's the first fully undetectable cloud-based cryptocurrency miner leveraging the Microsoft Azure Automation service without racking up any charges. Developed by Microsoft, it's a cloud-based automation service that allows users to automate the creation, deployment, monitoring, and maintenance of resources in Azure.

A threat actor, presumably from Tunisia, has been linked to a new campaign targeting exposed Jupyter Notebooks in a two-fold attempt to illicitly mine cryptocurrency and breach cloud environments....