Security News

Please turn on your JavaScript for this page to function normally. OAuth apps have become prominent in several attack groups' TTPs in recent years.

OAuth allows users to grant another application limited access to their resources - such as personal data, online accounts, and other sensitive items in SaaS environments - without sharing their credentials. OAuth is crucial in enabling seamless and secure connections between SaaS applications.

Multiple information-stealing malware families are abusing an undocumented Google OAuth endpoint named "MultiLogin" to restore expired authentication cookies and log into users' accounts, even if an account's password was reset. These cookies would allow the cybercriminals to gain unauthorized access to Google accounts even after the legitimate owners have logged out, reset their passwords, or their session has expired.

OAuth is an especially appealing target for criminals in cases where compromised accounts don't have strong authentication in place, and user permissions allow them to create or modify OAuth applications. Microsoft, in a threat intel report, details one cyber crime crew it tracks as Storm-1283 that used a compromised account to create an OAuth application and deploy VMs for crypto mining, while also racking up between $10,000 and $1.5 million in Azure compute fees.

Attackers are compromising high-privilege Microsoft accounts and abusing OAuth applications to launch a variety of financially-motivated attacks. Microsoft Threat Intelligence has observed a number of attacks that started with attackers compromising poorly secured accounts that have permissions to create, modify, and grant high privileges to OAuth applications.
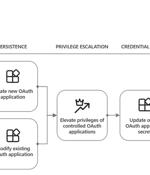
Microsoft has warned that adversaries are using OAuth applications as an automation tool to deploy virtual machines (VMs) for cryptocurrency mining and launch phishing attacks. "Threat actors...

Microsoft warns that financially-motivated threat actors are using OAuth applications to automate BEC and phishing attacks, push spam, and deploy VMs for cryptomining. Recent incidents investigated by Microsoft Threat Intelligence experts revealed that attackers mainly target user accounts that lack robust authentication mechanisms in phishing or password-spraying attacks, focusing on those with permissions to create or modify OAuth apps.
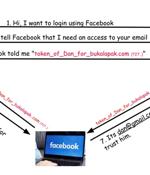
Critical security flaws have been disclosed in the Open Authorization (OAuth) implementation of popular online services such as Grammarly, Vidio, and Bukalapak, building upon previous shortcomings...
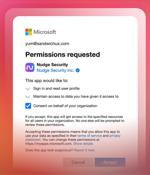
An even better practice would be to tailor your Google or Microsoft settings to require administrative approval for any new grant before employees can start using it, giving your team time to investigate and catch anything suspicious. While reviewing new OAuth grants can help you detect issues early on, oversight shouldn't end once an OAuth grant is in place.

Researchers at web coding security company SALT just published a fascinating description of how they found an authentication bug dubbed CVE-2023-28131 in a popular online app-building coding toolkit known as Expo. Expo itself adds a wrapper around the verification process, so that it handles the authentication and the validation for you, ultimately passing a magic access token for the desired website back to the app or website you're connecting from.