Security News

Microsoft announced today that Windows Extended Protection will be enabled by default on servers running Exchange Server 2019 starting this fall after installing the 2023 H2 Cumulative Update. Extended Protection is a feature that strengthens Windows Server auth functionality to mitigate authentication relay or "Man in the middle" attacks.

Microsoft says the recent wave of blue screens impacting some Windows users is not caused by issues in its August 2023 optional updates. Microsoft first acknowledged this known issue on Wednesday, saying that affected platforms include Windows 11 22H2 and Windows 10 21H2/22H2.
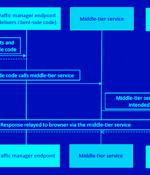
Cybersecurity researchers have discovered a case of privilege escalation associated with a Microsoft Entra ID application by taking advantage of an abandoned reply URL. "An attacker could leverage this abandoned URL to redirect authorization codes to themselves, exchanging the ill-gotten authorization codes for access tokens," Secureworks Counter Threat Unit said in a technical report published last week. Reply URL, also called redirect URI, refers to the location where the authorization server sends the user once the app has been successfully authorized and granted an authorization code or access token.

PLUS: India calls for global action on AI and crypto; Vietnam seeks cybersecurity independence; China bans AI prescribing drugs Asia In Brief Taiwan-based infosec consultancy Team T5 has disputed...

Microsoft is experimenting with different approaches to introduce new users to Windows 11's features as soon as they complete the initial setup, also known as the "Out of Box Experience". This app serves as a personal guide through the new features in Windows 11, showcasing Dev Home for those who've opted for the 'Development Intent'.

Microsoft has identified a new hacking group it now tracks as Flax Typhoon that argets government agencies and education, critical manufacturing, and information technology organizations likely for espionage purposes. Operating since at least mid-2021, Flax Typhoon mainly targeted organizations in Taiwan, although Microsoft discovered some victims in Southeast Asia, North America, and Africa.

Even if you join the Microsoft 365 Insiders Beta channel to test the new feature, there is no guarantee that Python in Excel will be available, as Microsoft is rolling it out slowly to test the feature. The new Python in Excel feature brings a new 'PY' function that allows users to embed Python code directly in a cell to be executed like any macro or regular Excel function.

A legitimate-looking ad for Amazon in Google search results redirects visitors to a Microsoft Defender tech support scam that locks up their browser. Clicking on the Google ad will redirect the person to a tech support scam pretending to be an alert from Microsoft Defender stating that you are infected with the ads(exe).

Infosec in brief Someone at Microsoft has some explaining to do after a messed up DNS record caused emails sent from Hotmail accounts Microsoft Outlook Hotmail accounts to be rejected and directed to spam folders overnight beginning Thursday. Microsoft support forum advisors confirmed that the issue was known, which was further confirmed by a look at the Office service status page.

Hotmail users worldwide have problems sending emails, with messages flagged as spam or not delivered after Microsoft misconfigured the domain's DNS SPF record. The email issues began late last night, with users and admins reporting on Reddit, Twitter, and Microsoft forums that their Hotmail emails were failing due to SPF validation errors.