Security News

Cybersecurity researchers have shed light on a short-lived DarkGate malware campaign that leveraged Samba file shares to initiate the infections. Palo Alto Networks Unit 42 said the activity spanned the months of March and April 2024, with the infection chains using servers running public-facing Samba file shares hosting Visual Basic Script and JavaScript files.

Meet DodgeBox, son of StealthVector Chinese government-backed cyber espionage gang APT41 has very likely added a loader dubbed DodgeBox and a backdoor named MoonWalk to its malware toolbox,...

The China-linked advanced persistent threat group codenamed APT41 is suspected to be using an "Advanced and upgraded version" of a known malware called StealthVector to deliver a previously undocumented backdoor dubbed MoonWalk. The new variant of StealthVector - which is also referred to as DUSTPAN - has been codenamed DodgeBox by Zscaler ThreatLabz, which discovered the loader strain in April 2024.
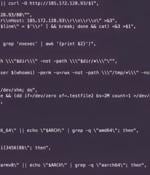
The vulnerability in question is CVE-2024-4577, which allows an attacker to remotely execute malicious commands on Windows systems using Chinese and Japanese language locales. The disclosure comes as Cloudflare said it recorded a 20% year-over-year increase in DDoS attacks in the second quarter of 2024, and that it mitigated 8.5 million DDoS attacks during the first six months.

The latest variants of the ViperSoftX info-stealing malware use the common language runtime (CLR) to load and execute PowerShell commands within AutoIt scripts to evade detection. [...]

Haifei Li discovered that threat actors have been distributing Windows Internet Shortcut Files to spoof legitimate-looking files, such as PDFs, but that download and launch HTA files to install password-stealing malware. An Internet Shortcut File is simply a text file that contains various configuration settings, such as what icon to show, what link to open when double-clicked, and other information.

Fujitsu Japan says an unspecified "Advanced" malware strain was to blame for a March data theft, insisting the strain was "Not ransomware", yet it hasn't revealed how many individuals are affected. Despite initially downplaying the likelihood of data theft, Fujitsu confirmed on Tuesday that affected individuals had been directly notified.

As ransomware crews increasingly shift beyond just encrypting victims' files and demanding a payment to unlock them, instead swiping sensitive info straight away, some of the more mature crime organizations are developing custom malware for their data theft. "Over the past year, we have witnessed major shifts in the ransomware space with the emergence of multiple new ransomware groups, each exhibiting unique goals, operational structures and victimology," the report's authors note.
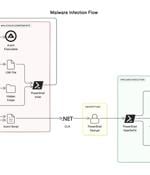
The sophisticated malware known as ViperSoftX has been observed being distributed as eBooks over torrents. "A notable aspect of the current variant of ViperSoftX is that it uses the Common Language Runtime to dynamically load and run PowerShell commands, thereby creating a PowerShell environment within AutoIt for operations," Trellix security researchers Mathanraj Thangaraju and Sijo Jacob said.

Military personnel from Middle East countries are the target of an ongoing surveillanceware operation that delivers an Android data-gathering tool called GuardZoo. GuardZoo is a modified version of an Android remote access trojan named Dendroid RAT that was first discovered by Broadcom-owned Symantec in March 2014.