Security News

Threat actors are exploiting the massive business disruption from CrowdStrike's glitchy update on Friday to target companies with data wipers and remote access tools. In an update today, CrowdStrike says that it "Is actively assisting customers" impacted by the recent content update that crashed millions of Windows hosts worldwide.

Cybersecurity firm CrowdStrike, which is facing the heat for causing worldwide IT disruptions by pushing out a flawed update to Windows devices, is now warning that threat actors are exploiting the situation to distribute Remcos RAT to its customers in Latin America under the guise of a providing a hotfix. The attack chains involve distributing a ZIP archive file named "Crowdstrike-hotfix.zip," which contains a malware loader named Hijack Loader that, in turn, launches the Remcos RAT payload. Specifically, the archive file also includes a text file with Spanish-language instructions that urges targets to run an executable file to recover from the issue.

A cybercriminal gang that researchers track as Revolver Rabbit has registered more than 500,000 domain names for infostealer campaigns that target Windows and macOS systems. One difference between the two is that DGAs are embedded in the malware strains and only some of the generated domains are registered, yet RDGAs remain with the threat actor, and all domains are registered.

Prolific Russian cybercrime syndicate FIN7 is using various pseudonyms to sell its custom security solution-disabling malware to different ransomware gangs. AvNeutralizer malware was previously thought to be solely linked to the Black Basta group, but fresh research has uncovered various underground forum listings of the malicious software now believed to be created by FIN7 operatives.

BeaverTail refers to a JavaScript stealer malware that was first documented by Palo Alto Networks Unit 42 in November 2023 as part of a campaign dubbed Contagious Interview that aims to infect software developers with malware through a supposed job interview process. Securonix is tracking the same activity under the moniker DEV#POPPER. Besides siphoning sensitive information from web browsers and crypto wallets, the malware is capable of delivering additional payloads like InvisibleFerret, a Python backdoor that's responsible for downloading AnyDesk for persistent remote access.
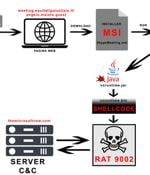
A China-linked threat actor called APT17 has been observed targeting Italian companies and government entities using a variant of a known malware referred to as 9002 RAT. The two targeted attacks took place on June 24 and July 2, 2024, Italian cybersecurity company TG Soft said in an analysis published last week. "The first campaign on June 24, 2024 used an Office document, while the second campaign contained a link," the company noted.

The DarkGate malware family has become more prevalent in recent months, after one of its main competitors was taken down by the FBI. The malware was discovered by endpoint security outfit enSilo's security maven Adi Zeligson in 2018 - but it has evolved over the years. Blackford's threat-hunting team recently detected a gang it tracks as TA571 using DarkGate to gain access to more than 1,000 organizations.

The Iranian-backed MuddyWatter hacking group has partially switched to using a new custom-tailored malware implant to steal files and run commands on compromised systems. "We discovered several versions of the malware being distributed, with differences between each version showing improvements and bug fixes," Check Point said.

Cybercriminals use Facebook business pages and advertisements to promote fake Windows themes that infect unsuspecting users with the SYS01 password-stealing malware. While using Facebook advertisements to push information-stealing malware is not new, the social media platform's massive reach makes these campaigns a significant threat.

The maintainers of the Exim mail transfer agent have fixed a critical vulnerability that currently affects around 1.5 million public-facing servers and can help attackers deliver malware to users. CVE-2024-39929 affects Exim releases up to and including 4.97.1, and has been fixed in Exim v4.98, which was released last week.