Security News

Network traffic continues to increase, and global internet bandwidth grew by 29% in 2021, reaching 786 Tbps. In addition to record traffic volumes, 95% of traffic is now encrypted according to Google. To help address these problems, many network security and operations teams are relying more heavily on machine learning technologies to identify faults, anomalies, and threats in network traffic.

Abstract: Given the computational cost and technical expertise required to train machine learning models, users may delegate the task of learning to a service provider. We show how a malicious learner can plant an undetectable backdoor into a classifier.

The report isn't just one researcher's work, or even one department's work, but the combined effort of SophosLabs, Sophos Managed Threat Response, Sophos Rapid Response, and Sophos Artificial Intelligence. Don't take Joe's word for it read the report and see how we live up to those three principles!

By using three tries, which is typically the maximum allowed number of attempts before the card is withheld, the researchers reconstructed the correct sequence for 5-digit PINs 30% of the time, and reached 41% for 4-digit PINs. This works even if the person is covering the pad with their hands.

Christopher Ford: Supervised and unsupervised learning are techniques that help to facilitate different use cases within the sphere of machine learning. In the machine learning world, labeled data is data that you, as a human, go through and describe to your machine learning system.

Figure A. Outside of the features Private Compute Core will bring to your device, one of the more important things it does is store data separate from all apps and services, while making that data available to the operating system when required. With Private Compute Core at work, that data is processed within its own sandbox, away from everything else, and then the captions are presented for your viewing.
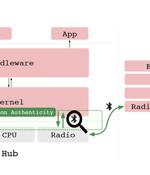
A group of academics has proposed a machine learning approach that uses authentic interactions between devices in Bluetooth networks as a foundation to handle device-to-device authentication reliably. Called "Verification of Interaction Authenticity", the recurring authentication scheme aims to solve the problem of passive, continuous authentication and automatic deauthentication once two devices are paired with one another, which remain authenticated until an explicit deauthentication action is taken, or the authenticated session expires.

eCloudvalley Technology announced that it is the first Amazon Web Services Consulting Partner to achieve the AWS Machine Learning Competency status in the ASEAN region. AWS Machine Learning Competency Partners have demonstrated expertise delivering machine learning solutions on the AWS Cloud.

Actually, pretty much all code does things not thought up by man, because man didn't really think through what man coded. The problem with any EMCM is it almost always falls into one of the "Arthur C Clarke's" eponymous cognative failing bear traps by those observing such a process.

Content delivery platform provider Akamai announced Wednesday platform security enhancements intended to increase cybersecurity protections for web applications, APIs and user accounts. Akamai said its machine learning algorithms leverage insights from a dataset of over 1.3 billion daily client interactions to automate threat detections, time-consuming tasks and security logic to help cybersecurity analysts make better decisions faster.