Security News

An unidentified whistleblower has provided several media organizations with access to leaked documents from NTC Vulkan - a Moscow IT consultancy - that allegedly show how the firm supports Russia's military and intelligence agencies with cyber warfare tools. According to The Guardian, this latest whistleblower chose to distribute the secret Russian documents due to anger over Russia's bloody invasion of Ukraine and a desire to see the information reveal some of what is going on inside Russia.

Thousands of pages of secret documents reveal how Vulkan's engineers have worked for Russian military and intelligence agencies to support hacking operations, train operatives before attacks on national infrastructure, spread disinformation and control sections of the internet. The company's work is linked to the federal security service or FSB, the domestic spy agency; the operational and intelligence divisions of the armed forces, known as the GOU and GRU; and the SVR, Russia's foreign intelligence organisation.

Twitter has taken down internal source code for its platform and tools that was leaked on GitHub for months.On Friday, GitHub complied with a DMCA infringement notice issued by Twitter because the leak exposed proprietary source code and internal tools, which could pose a security risk to Twitter.

Microsoft is working on a new XAML-based gallery view for Windows 11 File Explorer. This new Gallery option can be accessed via the right sidebar of File Explorer, letting you view your pictures in one place.

Money Lover is a finance app allowing users to manage their expenses and budgets that has been downloaded five million times on the Play Store, with the app also available for iOS and Windows. Money Lover allows users to create "Shared wallets" with specific users, like family members or coworkers, to log transactions to collaborate in expense logging and monitoring.
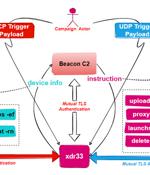
Unidentified threat actors have deployed a new backdoor that borrows its features from the U.S. Central Intelligence Agency's Hive multi-platform malware suite, the source code of which was released by WikiLeaks in November 2017. "This is the first time we caught a variant of the CIA Hive attack kit in the wild, and we named it xdr33 based on its embedded Bot-side certificate CN=xdr33," Qihoo Netlab 360's Alex Turing and Hui Wang said in a technical write-up published last week.

Twitter on Wednesday said that its investigation found "No evidence" that users' data sold online was obtained by exploiting any security vulnerabilities in its systems. "Based on information and intel analyzed to investigate the issue, there is no evidence that the data being sold online was obtained by exploiting a vulnerability of Twitter systems," the company said in a statement.

Twitter finally addressed reports that a dataset of email addresses linked to hundreds of millions of Twitter users was leaked and put up for sale online, saying that it found no evidence the data was obtained by exploiting a vulnerability in its systems. "In response to recent media reports of Twitter users' data being sold online, we conducted a thorough investigation and there is no evidence that data recently being sold was obtained by exploiting a vulnerability of Twitter systems," the company said.

Since July 22nd, 2022, threat actors and data breach collectors have been selling and circulating large data sets of scraped Twitter user profiles containing both private and public data on various online hacker forums and cybercrime marketplaces. These data sets were created in 2021 by exploiting a Twitter API vulnerability that allowed users to input email addresses and phone numbers to confirm whether they were associated with a Twitter ID. The threat actors then used another API to scrape the public Twitter data for the ID and combined this public data with private email addresses/phone numbers to create profiles of Twitter users.

Uber has suffered a new data breach after a threat actor leaked employee email addresses, corporate reports, and IT asset information stolen from a third-party vendor in a cybersecurity incident. Early Saturday morning, a threat actor named 'UberLeaks' began leaking data allegedly stolen from Uber and Uber Eats on a hacking forum known for publishing data breaches.