Security News
The North Korean threat actor known as Andariel has been observed employing an arsenal of malicious tools in its cyber assaults against corporations and organizations in the southern counterpart. Ariel, also known by the names Nicket Hyatt or Silent Chollima, is a sub-cluster of the Lazarus Group that's known to be active since at least 2008.

The Cisco Talos report exposes new malware used by the group to target Internet backbone infrastructure and healthcare organizations in the U.K. and the U.S. Two reports from cybersecurity company Cisco Talos provide intelligence about a new attack campaign from the North Korean threat actor Lazarus. The researchers observed the Lazarus group successfully compromise an internet backbone infrastructure provider in the U.K. in early 2023, deploying a new malware dubbed QuiteRAT. The initial compromise was done via exploitation of the CVE-2022-47966 vulnerability, which affects Zoho's ManageEngine ServiceDesk.

North Korean state-sponsored hackers Lazarus Group have been exploiting a ManageEngine ServiceDesk vulnerability to target internet backbone infrastructure and healthcare institutions in Europe and the US. The group leveraged the vulnerability to deploy QuiteRAT, downloaded from an IP address previously associated with the Lazarus hacking group. The malware Cisco Talos researchers dubbed QuiteRAT is a simple remote access trojan that's similar to Lazarus Group's MagicRAT malware, only smaller in size.
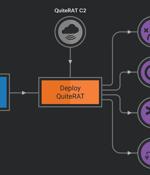
The North Korea-linked threat actor known as Lazarus Group has been observed exploiting a now-patched critical security flaw impacting Zoho ManageEngine ServiceDesk Plus to distribute a remote access trojan called such as QuiteRAT. Targets include internet backbone infrastructure and healthcare entities in Europe and the U.S., cybersecurity company Cisco Talos said in a two-part analysis published today. What's more, a closer examination of the adversary's recycled attack infrastructure in its cyber assaults on enterprises has led to the discovery of a new threat dubbed CollectionRAT. The fact that the Lazarus Group continues to rely on the same tradecraft despite those components being well-documented over the years underscores the threat actor's confidence in their operations, Talos pointed out.

The North Korean criminal gang Lazarus Group has been blamed for last weekend's attack on Atomic Wallet that drained at least $35 million in cryptocurrency from private accounts. The researchers added that the "Stolen assets are being laundered using specific services, including the Sinbad mixer, which have also been used to launder the proceeds of past hacks perpetrated by the Lazarus Group." In addition, the stolen assets were mingled in wallets that also hold cryptocurrency stolen in previous attacks by the Lazarus Group.
The infamous Lazarus Group actor has been targeting vulnerable versions of Microsoft Internet Information Services servers as an initial breach route to deploy malware on targeted systems. The findings come from the AhnLab Security Emergency response Center, which detailed the advanced persistent threat's continued abuse of DLL side-loading techniques to deploy malware.

The notorious North Korea-aligned state-sponsored actor known as the Lazarus Group has been attributed to a new campaign aimed at Linux users. The attacks are part of a persistent and long-running activity tracked under the name Operation Dream Job, ESET said in a new report published today.

The North Korea-linked Lazarus Group has been observed weaponizing flaws in an undisclosed software to breach a financial business entity in South Korea twice within a span of a year. While the first attack in May 2022 entailed the use of a vulnerable version of a certificate software that's widely used by public institutions and universities, the re-infiltration in October 2022 involved the exploitation of a zero-day in the same program.
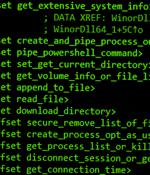
A new backdoor associated with a malware downloader named Wslink has been discovered, with the tool likely used by the notorious North Korea-aligned Lazarus Group, new findings reveal. The payload, dubbed WinorDLL64 by ESET, is a fully-featured implant that can exfiltrate, overwrite, and delete files; execute PowerShell commands; and obtain comprehensive information about the underlying machine.

The FBI has confirmed what cybersecurity researchers have been saying for months: the North Korean-sponsored Lazarus Group was behind the theft last year of $100 million in crypto assets from blockchain startup Harmony. In its January 23 statement on the matter, the FBI said the attack on Harmony was part of a North Korean malware campaign named "TraderTraitor."