Security News

The European Court of Human Rights has ruled that laws requiring crippled encryption and extensive data retention violate the European Convention on Human Rights - a decision that may derail European data surveillance legislation known as Chat Control. The Court issued a decision on Tuesday stating that "The contested legislation providing for the retention of all internet communications of all users, the security services' direct access to the data stored without adequate safeguards against abuse and the requirement to decrypt encrypted communications, as applied to end-to-end encrypted communications, cannot be regarded as necessary in a democratic society."

"Bad actors are using AI-generated voices in unsolicited robocalls to extort vulnerable family members, imitate celebrities, and misinform voters. We're putting the fraudsters behind these robocalls on notice," said FCC Chairwoman Jessica Rosenworcel.While currently, State Attorneys Generals can target the outcome of an unwanted AI-voice generated robocall-such as the scam or fraud they are seeking to perpetrate-this action now makes the act of using AI to generate the voice in these robocalls itself illegal, expanding the legal avenues through which state law enforcement agencies can hold these perpetrators accountable under the law.

The U.S. State Department said it's implementing a new policy that imposes visa restrictions on individuals who are linked to the illegal use of commercial spyware to surveil civil society...

Global crime networks have set up shop in autonomous territories run by armed gangs across Southeast Asia, and are using them to host physical and online casinos that, in concert with crypto exchanges, have led to an explosion of money laundering, cyberfraud, and cybercrime across the region and beyond. The scenario above was outlined on Monday by the United Nations Office on Drugs and Crime in a new report [PDF] titled "Casinos, Money Laundering, Underground Banking, and Transnational Organized Crime in East and Southeast Asia: A Hidden and Accelerating Threat."

The U.S. Department of Justice (DoJ) on Tuesday said it reached a settlement with VoIP service provider XCast over allegations that it facilitated illegal telemarketing campaigns since at least...

More details have emerged about a botnet called AVRecon, which has been observed making use of compromised small office/home office routers as part of a multi-year campaign active since at least May 2021. AVRecon was first disclosed by Lumen Black Lotus Labs earlier this month as malware capable of executing additional commands and stealing victim's bandwidth for what appears to be an illegal proxy service made available for other actors.

A VoIP provider was at the heart of billions of robocalls made over the past five years that broke a slew of US regulations, from enabling telemarketing scams to calling numbers on the National Do Not Call Registry, it is claimed. Los-Angeles-based XCast Labs allowed robocalls from telemarketers to flow through its voice-over-IP network to folks despite multiple warnings over several years that many of the calls ran afoul of the America's Telemarketing Sales Rule, the FTC alleged in a 13-page complaint [PDF] filed May 12 in a California federal court.
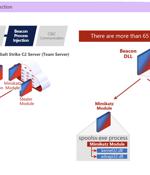
Microsoft said it teamed up with Fortra and Health Information Sharing and Analysis Center to tackle the abuse of Cobalt Strike by cybercriminals to distribute malware, including ransomware. While Cobalt Strike, developed and maintained by Fortra, is a legitimate post-exploitation tool used for adversary simulation, illegal cracked versions of the software have been weaponized by threat actors over the years.

A large darknet marketplace focused on drugs and illegal substances, has been taken over by a smaller competitor named 'Kraken,' who claims to have hacked it on January 13, 2022. The Tor site of Solaris currently redirects to Kraken, while blockchain monitoring experts at Elliptic report no movements in the cryptocurrency addresses associated with the site after January 13, 2022.

The dark web is getting darker as cybercrime gangs increasingly shop their malware, phishing, and ransomware tools on illegal cybercrime markets. In 2022, threat actors preferred joining a RaaS for ransomware attacks as they tend to have more freedom and can deploy faster than private ransomware.