Security News
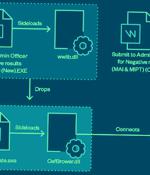
Attack chains mounted by the group commence with a spear-phishing email to deploy a wide range of tools for backdoor access, command-and-control, and data exfiltration. These messages come bearing with malicious lure archives distributed via Dropbox or Google Drive links that employ DLL side-loading, LNK shortcut files, and fake file extensions as arrival vectors to obtain a foothold and drop backdoors like TONEINS, TONESHELL, PUBLOAD, and MQsTTang.

Telecommunication providers in the Middle East are the subject of new cyber attacks that commenced in the first quarter of 2023. The intrusion set has been attributed to a Chinese cyber espionage actor associated with a long-running campaign dubbed Operation Soft Cell based on tooling overlaps.

A new credit card stealing hacking campaign is doing things differently than we have seen in the past by hiding their malicious code inside the 'Authorize.net' payment gateway module for WooCommcerce, allowing the breach to evade detection by security scans. To evade detection, the threat actors are now injecting malicious scripts directly into the site's payment gateway modules used to process credit card payments on checkout.

A joint cybersecurity advisory from the German Federal Office for the Protection of the Constitution and the National Intelligence Service of the Republic of Korea warn about Kimsuky's use of Chrome extensions to steal target's Gmail emails. Kimsuky is a North Korean threat group that uses spear phishing to conduct cyber-espionage against diplomats, journalists, government agencies, university professors, and politicians.

Security researchers have discovered attacks from an advanced threat actor that used "a previously unseen malicious framework" called CommonMagic and a new backdoor called PowerMagic. Researchers at cybersecurity company Kaspersky say that the hackers are interested in collecting data from victims in Donetsk, Lugansk, and Crimea.

Bitcoin ATM maker General Bytes disclosed that unidentified threat actors stole cryptocurrency from hot wallets by exploiting a zero-day security flaw in its software. "The attacker was able to upload his own java application remotely via the master service interface used by terminals to upload videos and run it using 'batm' user privileges," the company said in an advisory published over the weekend.

NET developers with cryptocurrency stealers delivered through the NuGet repository and impersonating multiple legitimate packages via typosquatting. NET developers who had their systems compromised, it could also be explained by the attackers' efforts to legitimize their malicious NuGet packages.

Hackers continue to target zero-day vulnerabilities in malicious campaigns, with researchers reporting that 55 zero-days were actively exploited in 2022, most targeting Microsoft, Google, and Apple products. According to Mandiant, most of last year's zero-day flaws were exploited by Chinese state-sponsored actors and most concerned operating systems, web browsers, and network management products.

The zero-day exploitation of a now-patched medium-security flaw in the Fortinet FortiOS operating system has been linked to a suspected Chinese hacking group. Threat intelligence firm Mandiant, which made the attribution, said the activity cluster is part of a broader campaign designed to deploy backdoors onto Fortinet and VMware solutions and maintain persistent access to victim environments.

A suspected Chinese hacking group has been linked to a series of attacks on government organizations exploiting a Fortinet zero-day vulnerability to deploy malware. The security flaw allowed threat actors to deploy malware payloads by executing unauthorized code or commands on unpatched FortiGate firewall devices, as Fortinet disclosed last week.